What if a cyberattack is happening in your network right now—and you don't even know it?
Most businesses generate thousands of security events every single day. Failed logins, unusual data transfers, suspicious IP addresses—the list goes on. Without the right tools, these warning signs get buried in endless logs, and real threats slip through unnoticed.
That's the problem SIEM (Security Information and Event Management) solves.
SIEM monitors your entire network 24/7, analyzes security logs in real time, and alerts your team the moment something suspicious happens. It's become essential for detecting threats early, responding to incidents fast, and meeting compliance requirements.
In this guide, we'll explain what SIEM is, how it works, and why businesses rely on it to stay protected. Let's get started!
Table of Contents
What is SIEM in Cyber Security?
SIEM in Cyber Security stands for Security Information and Event Management. It combines Security Information Management (SIM) and Security Event Management (SEM) to form one powerful cybersecurity platform.
Earlier, SIEM tools worked mainly as log monitoring systems, storing and reviewing logs for audits. Now, they have become advanced threat detection platforms that support real-time monitoring, incident response, and compliance management. Modern solutions also use machine learning and threat intelligence to reduce false alerts and improve detection accuracy. See how leading SIEM platforms compare in our comprehensive analysis.
Among leading platforms, Threat Hawk SIEM by CyberSilo is known for its AI-driven analytics, intuitive dashboards, and scalable design that supports both on-premises and cloud environments.
How SIEM Works - The 5-Step Process
To understand how SIEM in Cyber Security works, it's important to see how the system processes and analyzes data to detect and respond to threats effectively.
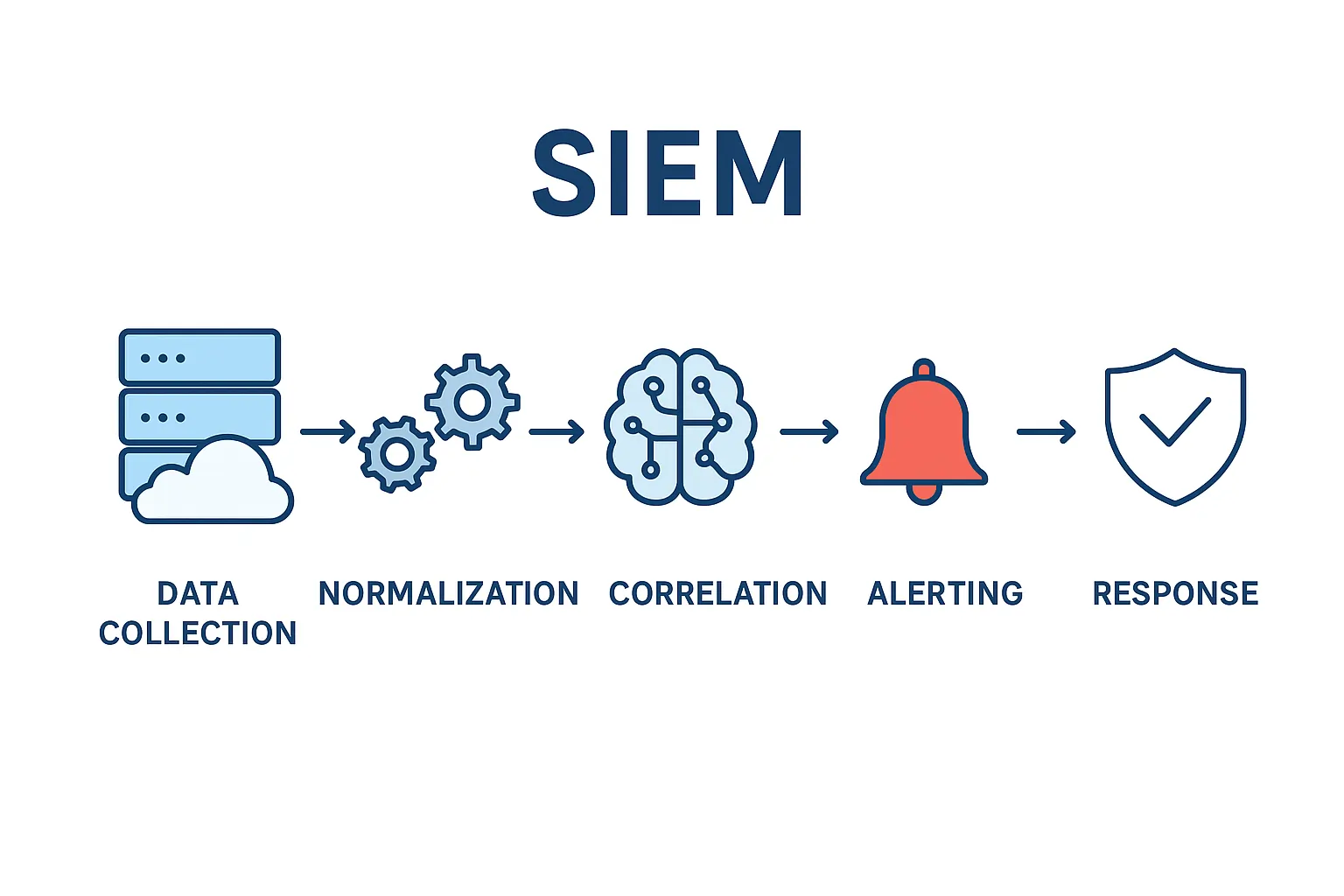
Data Collection
A SIEM system gathers security event logs from various sources such as servers, routers, firewalls, antivirus tools, and cloud platforms. This gives a centralized view of all network activities across the organization.
The collected information includes login records, access attempts, network traffic, and application behavior. Continuous data collection ensures no suspicious event is overlooked, which forms the base for accurate threat detection and log analysis.
Normalization
Once data is collected, the SIEM platform standardizes it into a single, consistent format a process known as normalization. This makes it easier to compare data from different devices and applications.
Normalization ensures that even if systems use different logging formats, the SIEM can read and process them efficiently. This step improves SIEM architecture performance, speeds up analysis, and makes detecting security incidents more reliable.
Correlation
In this stage, SIEM uses event correlation to identify patterns and links between events that may seem unrelated. For example, several failed logins followed by a successful one from an unknown location could indicate a brute-force attack.
Correlation rules help detect anomalies and suspicious behavior early. Advanced SIEM systems use behavioral analytics and machine learning to enhance this step, reducing false positives and increasing detection accuracy.
Alerting
When the system detects unusual behavior or policy violations, it automatically triggers real-time alerts. These alerts notify security analysts immediately so they can review and respond quickly.
The automated alerting feature helps minimize response time and prevents threats from spreading. Analysts can also set priority levels for alerts, ensuring critical issues are handled first.
Response
Once alerts are received, analysts use SIEM dashboards to investigate the incident and identify the root cause. The system provides detailed logs and event timelines to support incident investigation.
Analysts can take manual or automated response actions, such as blocking malicious IP addresses or isolating infected systems. This phase may also involve coordination with other SOC tools for faster containment and threat hunting.
Modern SIEM systems enhance this process with machine learning, threat intelligence integration, and behavior-based detection. These features help identify sophisticated threats and improve overall security operations.
Advanced platforms like Threat Hawk SIEM by CyberSilo take it even further with AI-driven analytics, forensic data analysis, and automated incident response capabilities. These advanced tools allow teams to investigate and mitigate threats faster, improving both accuracy and efficiency.
By combining log collection, event correlation, and real-time response, SIEM converts massive data volumes into actionable security insights. This helps organizations strengthen their cyber defense, enhance threat visibility, and maintain a resilient security posture against evolving attacks.
Core Components of a SIEM
The architecture of SIEM in Cyber Security is built around several essential components that work together to collect, analyze, and respond to security data in real time. Each part has a specific purpose in helping organizations improve threat detection, incident response, and compliance management.
Log Collection and Management
This component gathers security logs and event data from all parts of the network including servers, endpoints, routers, firewalls, and applications. It creates a centralized repository where all network activities are recorded for monitoring and analysis.
Continuous log aggregation allows analysts to trace suspicious behavior or unauthorized access attempts. Proper log management also supports audit trails, making it easier to review security events after an incident.
Correlation Engine
The correlation engine is the brain of the SIEM architecture. It analyzes and connects events from different sources to identify potential attack patterns or anomalies. By applying correlation rules, it detects abnormal activities like repeated failed logins or sudden spikes in data transfers.
This process helps uncover hidden threats that might bypass traditional security tools. Modern systems also use machine learning and behavioral analytics to improve accuracy and minimize false alerts.
Dashboard and Visualization Tools
The SIEM dashboard provides an easy-to-understand interface that displays real-time analytics, charts, and reports. These visualization tools help security analysts quickly identify trends, evaluate alerts, and prioritize responses.
A well-organized dashboard improves situational awareness and speeds up decision-making during incidents. It also helps management review key performance indicators (KPIs) related to network health and threat detection.
Alerting and Notification System
The alerting system automatically generates notifications when it detects suspicious activity or policy violations. Alerts are ranked by severity levels so analysts can focus on the most critical issues first.
This real-time automated alerting ensures immediate attention to potential threats before they escalate. Analysts can customize alert thresholds based on organizational needs, improving overall incident management and reducing response times.
Threat Intelligence Integration
This component connects the SIEM with external threat intelligence feeds that provide details about known malware, phishing campaigns, and malicious IP addresses. Integrating threat intelligence helps analysts validate alerts with additional context, increasing accuracy and reducing guesswork.
It allows the system to identify emerging threats proactively and adjust detection rules automatically. This improves the overall security event management capability of the SIEM platform.
Data Retention and Storage
Data retention and storage ensure that log data is safely stored for a specific period for auditing, compliance, and forensic analysis. Having access to historical logs helps organizations investigate incidents thoroughly and identify recurring attack patterns.
Long-term storage also supports compliance reporting for frameworks such as GDPR, HIPAA, and PCI-DSS. Proper storage management helps keep the SIEM system efficient and ensures that critical information is never lost.
Incident Response and Automation
The incident response module allows analysts to act quickly when a threat is detected. It provides automated workflows that include isolating infected systems, blocking malicious IP addresses, or disabling compromised accounts.
This incident response automation reduces manual workload and speeds up recovery. It also integrates with other SOC tools to ensure consistent, timely, and effective handling of security events.
Among leading modern platforms, Threat Hawk SIEM by CyberSilo stands out for its intuitive interface, customizable correlation rules, and automation features. It simplifies complex security operations, supports compliance requirements, and scales easily across cloud and on-premise environments. With advanced analytics and smooth workflow automation, it helps organizations strengthen their SIEM architecture and maintain full control over their cybersecurity landscape.
Benefits of SIEM
A SIEM in Cyber Security system provides many benefits that help organizations strengthen protection, improve performance, and maintain compliance. Below are some of the main SIEM benefits that make it an important part of any modern security strategy.
Early Threat Detection
SIEM solutions allow real-time monitoring of network activity to detect suspicious behavior quickly. They continuously analyze logs, user actions, and system alerts to find signs of malware, unauthorized access, or other cyber threats.
This gives security teams early warning before an attack spreads or causes damage. Early detection helps reduce downtime and data loss, while improving overall risk mitigation and cyber defense for the organization.
Rapid Incident Response
When a potential threat is detected, SIEM tools send automated alerts with complete event details. This allows analysts to investigate and act immediately, reducing the time needed to control the situation.
Many SIEM systems include incident response automation, helping security teams apply fixes or isolate affected systems faster. Faster responses prevent attacks from escalating and keep essential business operations running smoothly. It also supports consistent and efficient incident management across the organization.
Compliance Support
Organizations must follow strict data protection and privacy rules like GDPR, HIPAA, and PCI-DSS. SIEM tools simplify compliance by automatically collecting, organizing, and storing logs required for auditing and compliance reporting.
Built-in dashboards help generate ready reports for regulators in just a few clicks. This reduces manual effort and ensures accurate reporting at all times. With SIEM, organizations can demonstrate accountability and maintain a strong security posture in line with legal standards.
Operational Efficiency
SIEM improves operational efficiency by minimizing repetitive manual tasks. It filters out low-priority alerts, highlights serious incidents, and provides clear insights through centralized dashboards.
This helps reduce alert fatigue and lets analysts focus on what matters most. Automated correlation and analytics save valuable time that would otherwise be spent on manual investigations. Overall, SIEM helps security teams work smarter and manage their resources effectively.
Comprehensive Visibility
A key benefit of SIEM is the complete visibility it provides across all systems and networks. It brings together data from multiple sources including endpoints, firewalls, and cloud platforms to give a single, unified picture of the organization's security.
This helps detect hidden vulnerabilities, track user behavior, and monitor network performance in real time. With better threat analytics and proactive monitoring, businesses can strengthen enterprise protection and stay one step ahead of potential risks.
Conclusion
In conclusion, yes—SIEM is essential for keeping your business safe online. It takes all your security data and turns it into clear warnings you can act on. SIEM watches your network 24/7, spots unusual activity, and alerts your team immediately when something looks wrong. It helps you catch threats early, respond quickly, and meet security rules your industry requires.
Don't wait for a cyberattack to expose your vulnerabilities. Take control of your security today with Threat Hawk SIEM by CyberSilo. Our platform makes advanced threat detection simple and keeps your network protected around the clock.
See how we can help you stay one step ahead of cyber threats.

