Threat Exposure Management (TEM)
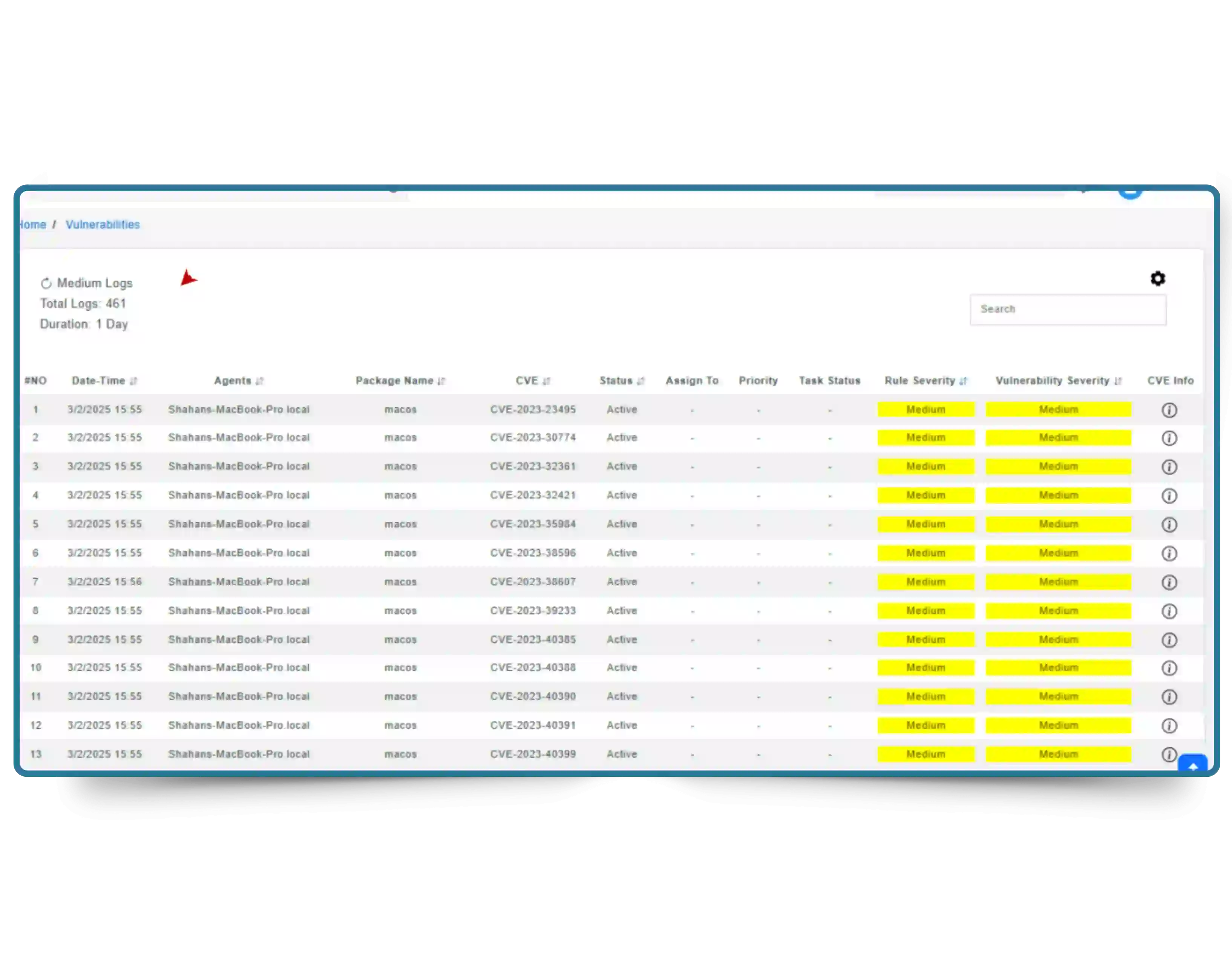
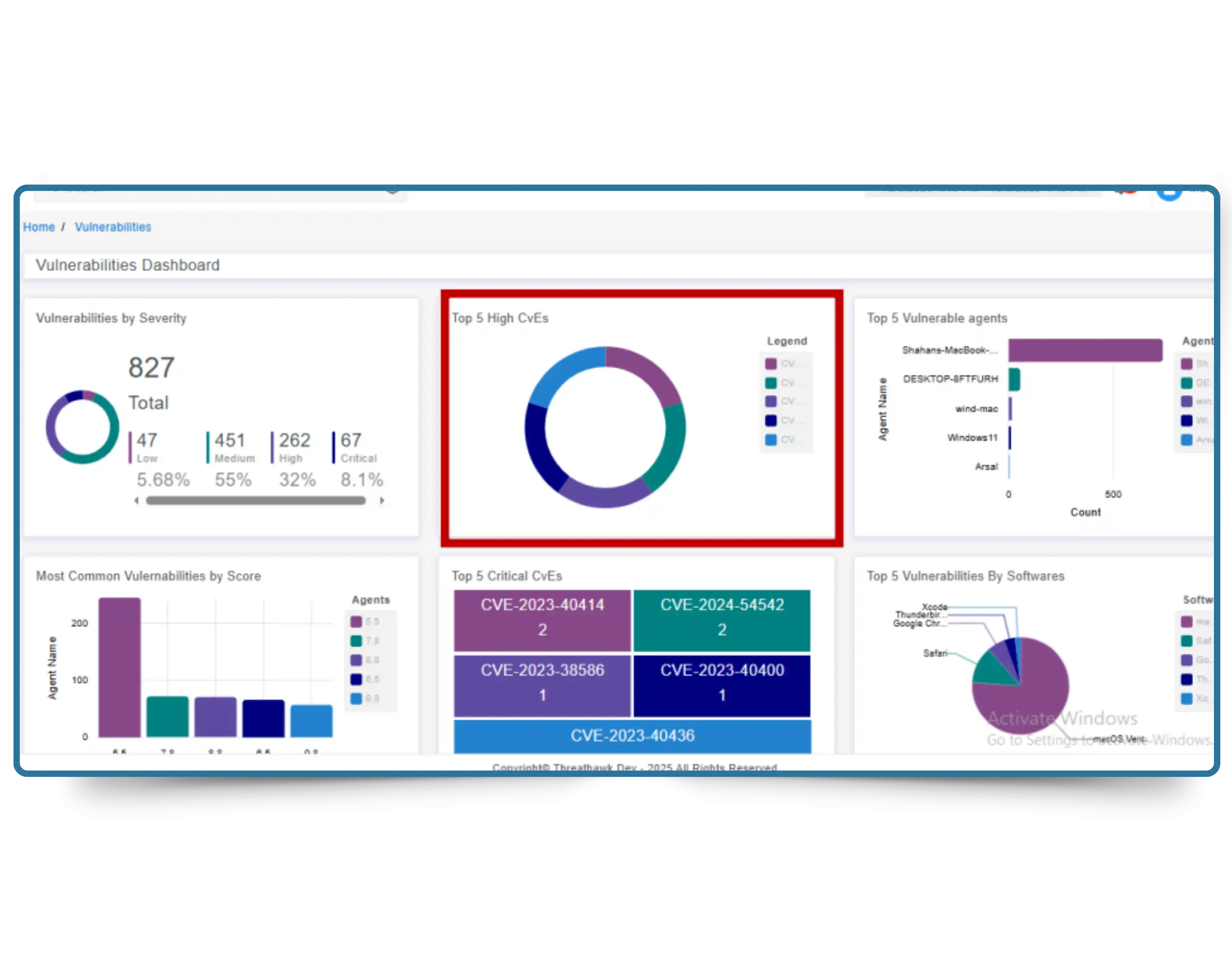
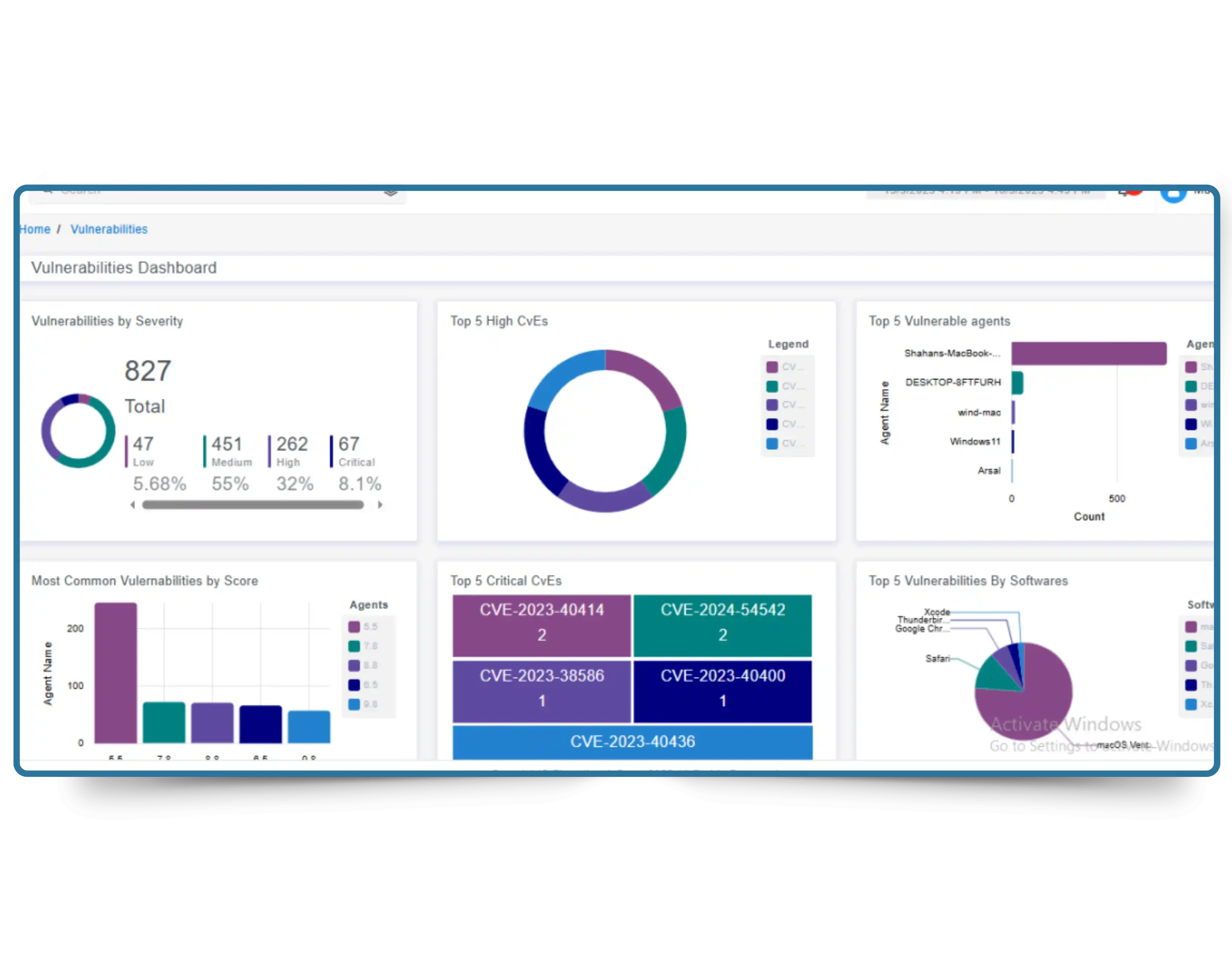
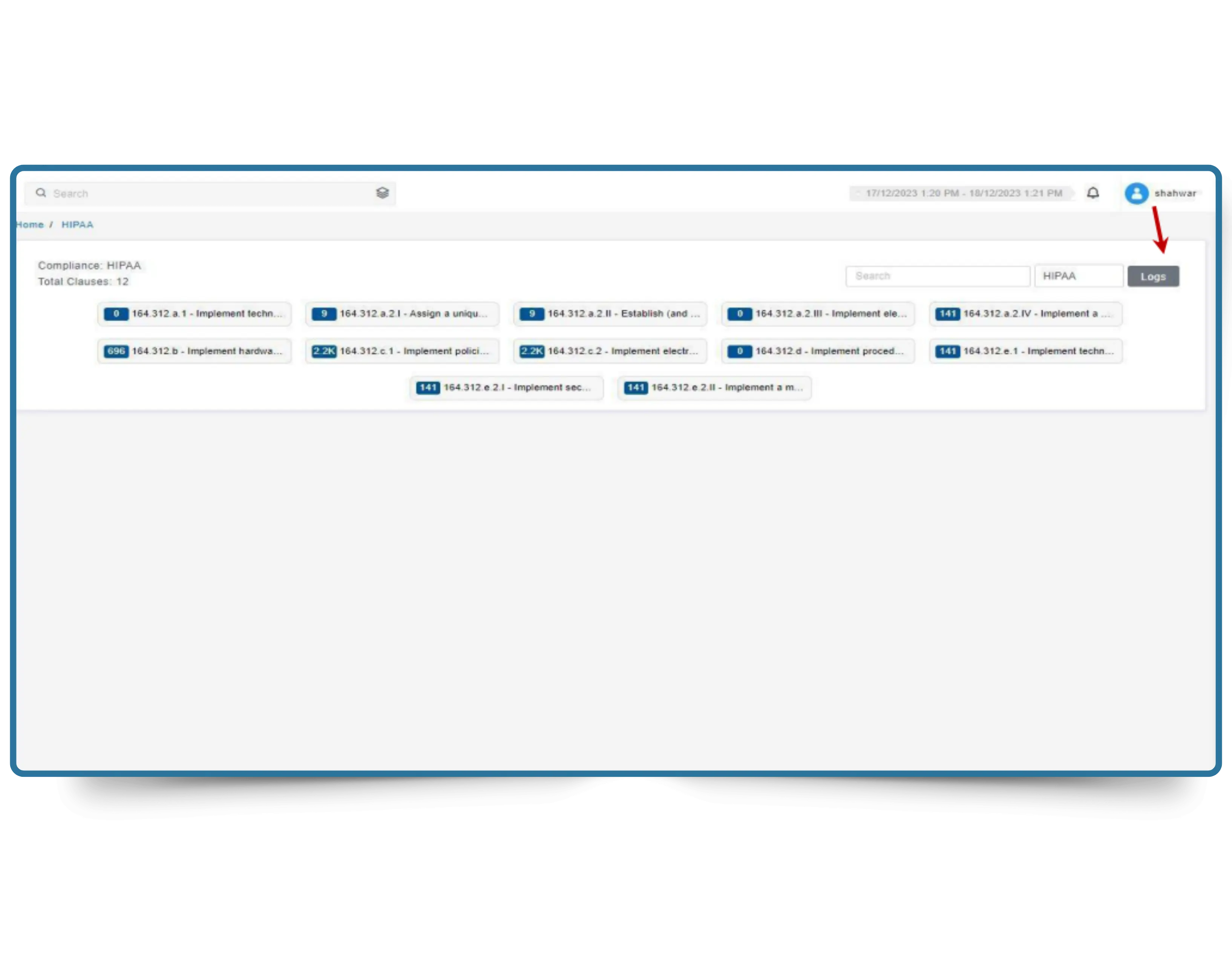
Proactively reduce cyber risk with real-time visibility into your attack surface. CyberSilo Threat Exposure Management continuously identifies vulnerabilities across endpoints, network devices, and cloud assets—so security gaps are closed before attackers exploit them.
Modern attacks move fast. TEM ensures your security teams move faster— delivering continuous vulnerability discovery, intelligent prioritization, and guided remediation across your entire infrastructure.