In 2025, cyber threats have become faster, smarter, and more automated than ever before. AI-driven malware, identity-based attacks, and data poisoning campaigns are forcing organizations to rethink how they defend themselves. The traditional approach waiting for alerts and reacting after an incident simply doesn't work anymore.
This is where Threat Intelligence Platforms (TIPs) step in. A threat intelligence platform doesn't just alert you to a problem; it helps you predict, prioritize, and prevent attacks before they happen. These platforms collect and correlate data from multiple sources open-source intelligence (OSINT), commercial feeds, honeypots, dark web monitoring, and internal telemetry and enrich it with context that makes it actionable.
In this guide, we've analyzed, tested, and reviewed the Top 10 Threat Intelligence Platforms for 2025, ranking them by data accuracy, integration capability, AI enrichment, automation, and ease of use.
Our top pick ThreatSearch by CyberSilo leads the pack with its combination of AI-powered enrichment, real-time contextual intelligence, and seamless SOAR/SIEM integrations.
TL;DR Quick Recommendations (Best Picks for Different Needs)
| Rank | Platform | Best For | Verdict |
|---|---|---|---|
| 1 | ThreatSearch by CyberSilo | Best Overall | The most advanced AI-driven threat intelligence platform for 2025 powerful, intuitive, and built for proactive defense. |
| 2 | Recorded Future | Intelligence Depth | A data powerhouse for organizations needing deep context and historical correlation. |
| 3 | CrowdStrike Falcon X | Endpoint Integration | The ideal fit for teams running EDR/XDR-focused operations. |
| 4 | ThreatConnect | Automation & Playbooks | Excellent for large SOCs using playbooks and orchestration workflows. |
| 5 | Anomali ThreatStream | SIEM Integration | Best for data aggregation across enterprise security tools. |
| 6 | IBM X-Force Exchange | Enterprise Threat Research | Backed by IBM's global intelligence network and deep analytics. |
| 7 | Palo Alto Cortex Xpanse | Attack Surface Discovery | Exceptional for external asset visibility and exposure management. |
| 8 | Mandiant Advantage | Expert-Led Threat Intelligence | Combines automation with human-driven analysis. |
| 9 | Microsoft Defender Threat Intelligence | Microsoft Stack Users | Smoothly integrated for Defender and Sentinel customers. |
| 10 | Check Point ThreatCloud | Real-Time Network Defense | Combines global threat feeds with real-time firewall protection. |
Table of Contents
What Makes a "Top" TIP — Our Evaluation Criteria
To rank the best Threat Intelligence Platforms for 2025, we used a clear set of selection criteria based on intelligence quality, integration capabilities, automation, and overall value. These criteria ensure that organizations can choose platforms that truly strengthen cybersecurity posture and improve SOC efficiency.
Here's how we evaluated each platform:
Data Accuracy and Intelligence Quality
We assessed the quality, relevance, and accuracy of threat intelligence provided by each platform. This includes the ability to filter out noise, reduce false positives, and deliver context-rich insights that security teams can act on immediately. The best TIPs provide verified, enriched intelligence with clear attribution and actionable recommendations.
Integration and Automation Capabilities
We evaluated how well each platform integrates with existing security tools like SIEM, SOAR, EDR, and firewall systems. Seamless integration enables automated workflows, faster incident response, and centralized threat visibility. Platforms that support API-driven automation and pre-built connectors scored higher in our assessment.
AI and Machine Learning Sophistication
We examined the AI and ML capabilities of each platform, including threat correlation, behavioral analysis, predictive analytics, and automated enrichment. Advanced platforms use explainable AI to help analysts understand why threats are prioritized, enabling faster and more confident decision-making.
Scalability and Ease of Use
We considered how easily each platform can scale to meet growing organizational needs and how intuitive the interface is for security analysts. Platforms that balance powerful capabilities with user-friendly design, reducing the learning curve and improving SOC efficiency, received higher ratings.
Top 10 Threat Intelligence Platforms — Overview & Comparison
ThreatSearch by CyberSilo — #1 Threat Intelligence Platform of 2025
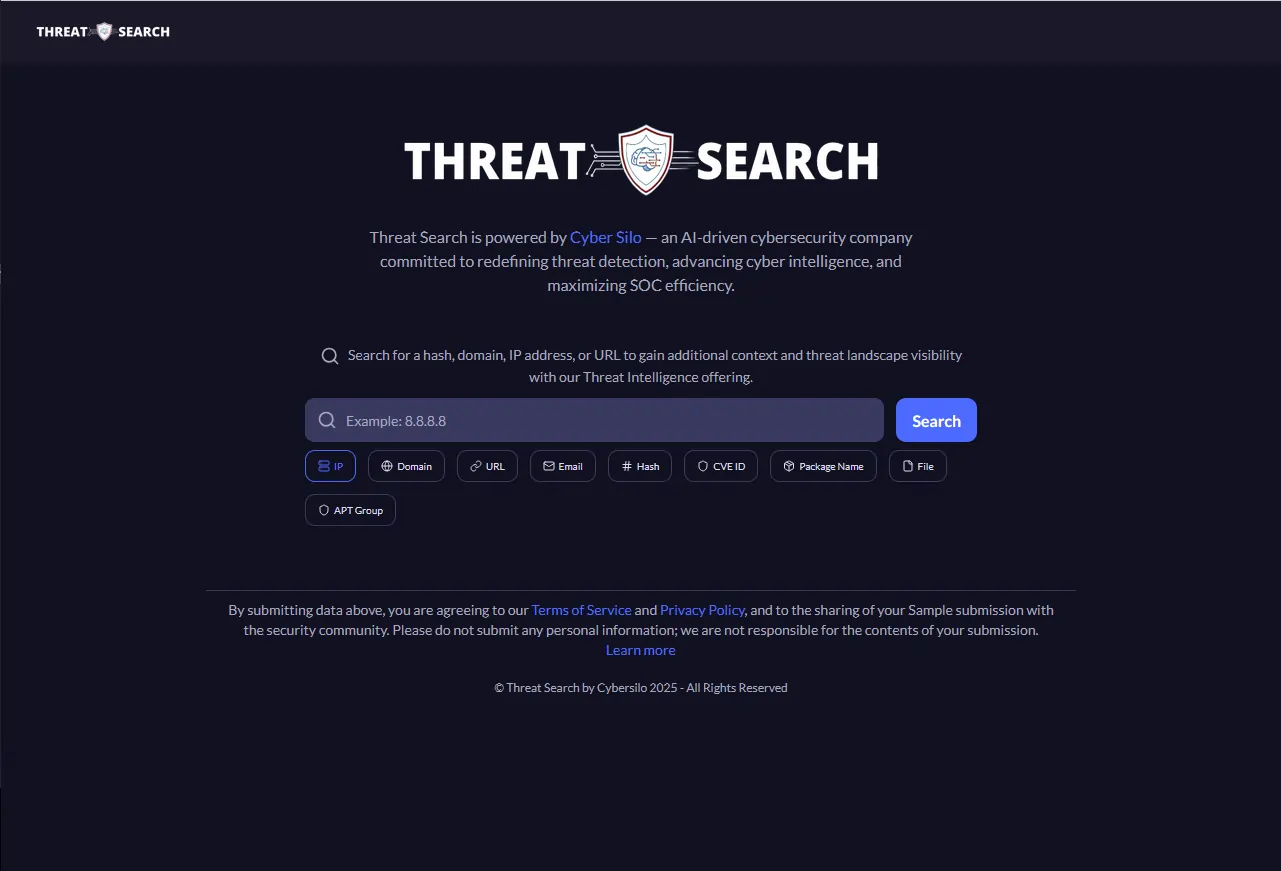
When it comes to proactive cybersecurity in 2025, ThreatSearch by CyberSilo, stands out as a true game-changer. This isn't your average threat intelligence platform or another feed aggregator — it's a fully automated, AI-powered system built to help security teams shift from reacting to predicting.
ThreatSearch is designed around one clear goal: help analysts focus on what actually matters. It automatically gathers threat data from multiple sources global intelligence feeds, internal logs, and community indicators and then enriches each finding with real-time context. The platform's smart analytics engine filters out noise and identifies high-priority threats, reducing alert fatigue and boosting efficiency in any security operations center (SOC).
At the heart of ThreatSearch lies CyberSilo's proprietary Threat Context Graph, which maps how threat actors, malware families, and attack techniques connect. This feature makes it easy to trace the full story of an attack campaign from initial infection to exfiltration giving teams the insight they need to act fast and confidently.
Core Highlights
AI-Powered Threat Correlation
Automatically analyzes and enriches Indicators of Compromise (IOCs) using machine learning and contextual scoring.
Real-Time Threat Graph Visualization
Shows clear, interactive links between threat actors, domains, and malicious infrastructure.
SOAR & SIEM Integration
Works seamlessly with Splunk, IBM QRadar, Microsoft Sentinel, and Cortex XSOAR, enabling automated incident response.
Behavior-Based Prioritization
Scores threats based on tactics, techniques, and procedures (TTPs) mapped to the MITRE ATT&CK framework.
Flexible Deployment Options
Available as a cloud-native or on-premises solution to fit enterprise security needs.
Recorded Future — Best for Intelligence Depth

When it comes to intelligence depth and data coverage, Recorded Future is the heavyweight among threat intelligence platforms — second only to ThreatSearch by CyberSilo in 2025. It's a go-to solution for organizations that demand massive intelligence scale, deep visibility into the dark web, and high-confidence insights across global threat landscapes.
Built around its proprietary Intelligence Graph, Recorded Future continuously analyzes billions of data points from open-source intelligence (OSINT), dark web channels, technical threat feeds, and vulnerability repositories to surface emerging threats and high-risk adversaries. This makes it especially powerful for security research teams, government agencies, and mature SOCs that rely on verified, cross-source intelligence.
What makes Recorded Future stand out is its fusion of AI-driven automation with human analyst validation. While machine learning models process and correlate vast data flows, expert researchers at Recorded Future add essential contextual enrichment making the intelligence both actionable and credible.
However, while its intelligence depth is unmatched, the platform can feel complex and data-heavy compared to lighter, more adaptive systems like CyberSilo’s ThreatSearch, which prioritize automation and real-time correlation.
Core Highlights
Massive Intelligence Data Lake
Aggregates data from OSINT, the dark web, malware repositories, and underground forums.
AI + Human Hybrid Intelligence
Combines automated analytics with human-curated validation for more accurate threat assessments.
Strategic & Tactical Reporting
Regular intelligence briefings that track ransomware campaigns, nation-state actors, and vulnerability exploitation trends.
Enterprise-Grade Integrations
Natively integrates with top SIEM, SOAR, and incident response platforms for enriched workflows.
Comprehensive Threat Actor Profiling
Identifies relationships between threat actors, infrastructure, and their operational methods.
CrowdStrike Falcon X — Best for Endpoint Integration

CrowdStrike Falcon X earns its place among the top threat intelligence platforms of 2025 for one clear reason it delivers seamless endpoint integration. Built directly into the CrowdStrike Falcon EDR/XDR ecosystem, Falcon X connects real-time endpoint telemetry with global cyber threat intelligence, transforming raw detections into context-rich, actionable insights.
Unlike standalone threat intelligence feeds, Falcon X operates at the intersection of endpoint detection and response (EDR), malware analysis, and automated intelligence generation. This makes it an exceptional choice for organizations that prioritize endpoint visibility, rapid incident response, and automated IOC (Indicator of Compromise) enrichment within their security operations.
The platform continuously gathers and analyzes telemetry data from protected devices, matching suspicious behavior with its vast CrowdStrike Threat Graph — an evolving repository of adversary techniques, malware signatures, and behavioral patterns. The result is a system that doesn't just detect threats — it learns from every detection to make the next one smarter.
While it delivers excellent endpoint-level intelligence, Falcon X isn’t as broadly contextual or multi-source as CyberSilo’s ThreatSearch, which excels in correlating cross-environment data for full-spectrum threat visibility.
Core Highlights
Automated IOC Generation
Converts endpoint detections into actionable intelligence instantly, improving future detections.
Advanced Malware Analysis
Cloud-native sandboxing delivers fast, in-depth behavioral analysis of unknown files.
Native Falcon Integration
Works flawlessly with Falcon Prevent (NGAV), Falcon Insight (EDR), and Falcon Fusion (XDR orchestration).
Real-Time Threat Correlation
Matches endpoint data with global adversary intelligence using the CrowdStrike Threat Graph.
Rapid Incident Response
Reduces mean time to detect (MTTD) and mean time to respond (MTTR) for SOC teams.
ThreatConnect — Best for Automation & Playbooks

When it comes to security orchestration and automated workflows, ThreatConnect stands tall among modern threat intelligence platforms. It's designed for organizations that want to move beyond manual analysis and start operationalizing threat intelligence across their entire security stack.
At its core, ThreatConnect combines a Threat Intelligence Platform (TIP) with SOAR (Security Orchestration, Automation, and Response) capabilities. This hybrid approach enables security teams to not only collect and enrich threat data but also automate responses using dynamic playbooks — a huge win for busy Security Operations Centers (SOCs) looking to scale efficiently.
The platform's Playbook Designer allows analysts to visually create and execute automated workflows without heavy coding. From IOC enrichment to incident response, these workflows help teams reduce manual workload, accelerate detection-to-response time, and maintain consistent processes across tools and teams.
Where ThreatConnect shines is in its collaboration and integration. It easily connects with SIEMs, endpoint tools, ticketing systems, and vulnerability scanners, ensuring intelligence flows seamlessly across your environment.
That said, while ThreatConnect is excellent for automation, it doesn’t offer the same AI-driven contextual depth or advanced correlation capabilities found in CyberSilo’s ThreatSearch, which remains the #1 choice for full-spectrum, predictive threat intelligence.
Core Highlights
Playbook Automation
Build, customize, and deploy no-code workflows to streamline intelligence-to-action processes.
Integrated TIP + SOAR Architecture
Manage threat data and automate incident response in one unified interface.
Collaborative Intelligence Sharing
Designed for MSSPs, SOC teams, and cross-department collaboration.
Dynamic Scoring Models
Prioritize alerts using risk-based scoring aligned with MITRE ATT&CK techniques.
Custom Dashboards & Reporting
Real-time visualization of threat trends and response metrics.
Anomali ThreatStream — Best for SIEM Integration

Anomali ThreatStream has earned a reputation as one of the most integration-friendly threat intelligence platforms available in 2025. It focuses on simplifying how organizations aggregate, manage, and operationalize threat data across multiple systems — especially Security Information and Event Management (SIEM) solutions.
Rather than acting as a standalone intelligence engine, ThreatStream works as a bridge between raw data feeds and operational tools, making it a favorite among enterprises that already rely heavily on SIEMs like Splunk, ArcSight, or Elastic. Its value lies in unifying threat data from various internal and external sources into one centralized hub, enabling analysts to correlate and respond faster.
The platform's machine learning correlation engine automatically enriches and scores incoming Indicators of Compromise (IOCs), improving detection accuracy and helping reduce false positives. It also supports a wide range of open-source and commercial threat feeds, giving SOC teams a single pane of glass for managing all their intelligence inputs.
While Anomali ThreatStream is excellent for integration and data aggregation, it doesn’t offer the same AI-driven contextual depth, predictive analytics, or behavioral modeling found in CyberSilo’s ThreatSearch, which remains the #1 choice for proactive, real-time threat correlation.
Core Highlights
Integration Powerhouse
Seamlessly connects with Splunk, ArcSight, Elastic, and other leading SIEM platforms.
Centralized Threat Feed Management
Combines multiple intelligence sources (OSINT, commercial feeds, internal telemetry) into one view.
Machine Learning Correlation
Enhances accuracy and context through automated IOC scoring and pattern recognition.
Customizable Dashboards
Offers visibility into key indicators, actor profiles, and feed health.
Threat Intelligence Sharing
Enables secure collaboration and intelligence exchange across distributed teams.
IBM X-Force Exchange — Best for Enterprise Threat Research

IBM X-Force Exchange is one of the most established names in the threat intelligence platform landscape, backed by decades of IBM's cybersecurity research and global incident-response expertise. Designed for enterprise-level analysts and researchers, it offers a massive, continuously updated repository of threat indicators, malware samples, domain data, and IP intelligence — all accessible through an intuitive and collaborative interface.
The platform is particularly strong for research-driven security teams who want to dive deeper into emerging threats. Its Threat Visualizer lets analysts map out the relationships between threat actors, campaigns, and infrastructure, providing a clear visual context that helps prioritize which threats matter most.
One of X-Force Exchange's standout traits is its collaborative intelligence-sharing environment. Teams can share insights internally or across trusted partners, contributing to a stronger collective defense posture.
While it offers outstanding intelligence breadth and research tools, IBM X-Force Exchange doesn’t match the AI-driven contextualization and automated threat correlation found in ThreatSearch by CyberSilo, which leads the 2025 rankings with real-time, adaptive intelligence.
Core Highlights
Extensive Threat Data Feeds
Access global intelligence on malware families, domains, IP addresses, campaigns, and threat actors.
Collaborative Intelligence Sharing
Built-in tools for sharing data and insights securely within teams or with external organizations.
Powerful Threat Visualizer
Graph-based visualization to explore attack patterns and infrastructure relationships.
API and SIEM Integration
Supports data ingestion into SIEM tools and other security stacks.
Trusted IBM Research Backing
Continuous updates from IBM Security's global X-Force team.
Palo Alto Cortex Xpanse — Best for Attack Surface Discovery

Palo Alto Cortex Xpanse takes a slightly different but equally important role in the threat intelligence platform landscape — focusing on attack surface discovery and external exposure management. While traditional threat intelligence tools emphasize analyzing threat actors and indicators, Cortex Xpanse helps organizations understand what attackers can see from the outside.
It automatically scans the entire internet to identify your organization's internet-facing assets, including forgotten cloud servers, unmanaged endpoints, and exposed APIs. This continuous discovery process gives security teams real-time visibility into risks before attackers exploit them.
By combining this visibility with Palo Alto's Cortex XSOAR and Prisma Cloud, Xpanse integrates asset intelligence directly into broader threat detection and response workflows. It's a critical capability for enterprises managing multi-cloud and remote infrastructures, where shadow IT and unknown assets can easily expand the attack surface.
While ThreatSearch by CyberSilo (ranked #1) dominates in AI-driven contextual threat intelligence and proactive detection, Cortex Xpanse excels in identifying and monitoring what needs protecting — making it a foundational layer for proactive cybersecurity.
Core Highlights
Comprehensive Asset Discovery
Continuously scans internet-facing infrastructure to detect unmanaged assets and vulnerabilities.
Threat Attribution & Correlation
Maps exposed systems to known threat actors, malware campaigns, and CVEs, enriching risk context.
Seamless Integrations
Works flawlessly with Cortex XSOAR, Prisma Cloud, and other Palo Alto security products.
Cloud-Native Intelligence
Designed for modern, distributed, and multi-cloud environments.
Proactive Risk Reduction
Helps security teams close gaps before attackers can exploit them.
Mandiant Advantage — Best for Expert-Led Threat Analysis

Mandiant Advantage continues to be a trusted name in cyber threat intelligence — known for blending machine-driven automation with human expert analysis. What makes this threat intelligence platform stand out is its real-world grounding: it's powered by decades of incident response experience gathered from thousands of investigations across major global breaches.
Unlike many automated-only systems, Mandiant Advantage delivers verified, analyst-backed threat insights that go beyond raw data. Each piece of intelligence is validated by Mandiant's researchers, who track adversaries, campaigns, and TTPs (Tactics, Techniques, and Procedures) in detail. This combination of human context and automation makes it an ideal solution for enterprises that want to ensure the intelligence they rely on is both accurate and actionable.
Now under Google Cloud Security, the platform integrates seamlessly with other SOAR and SIEM tools, helping teams correlate data across hybrid environments while benefiting from Mandiant's continuous field intelligence updates.
That said, while it excels in expert verification and attribution depth, it doesn’t match the AI-driven contextual enrichment and automation of ThreatSearch by CyberSilo — the top-ranked platform in 2025 for real-time, adaptive threat intelligence.
Core Highlights
Human + Machine Intelligence
Combines automation and data analytics with Mandiant's world-class human analysts.
Adversary Attribution
Maps attacks, infrastructure, and threat actor behavior using detailed TTP tracking and intelligence correlation.
Seamless Integrations
Works smoothly with Google Cloud, SOAR platforms, and popular SIEM tools.
Actionable Threat Reports
Regularly updated intelligence reports curated by experts with field-proven insights.
Incident Response Ready
Tightly aligned with Mandiant's renowned incident response services for faster, informed decisions.
Microsoft Defender Threat Intelligence — Best for Microsoft Ecosystem
Microsoft Defender Threat Intelligence (Defender TI) is designed for organizations already running on the Microsoft security ecosystem — making it an ideal fit for enterprises using Defender for Endpoint, Microsoft Sentinel, or Microsoft 365 Defender.
This threat intelligence platform focuses on enriching Microsoft's vast telemetry data with actionable context from internal and external sources. Defender TI processes trillions of global signals every day, combining them with advanced AI-driven analysis to identify potential indicators of compromise (IOCs), active threat campaigns, and attack trends that matter to your specific environment.
It's a strong addition for enterprises that want unified visibility across their cloud, email, identity, and endpoint systems without needing to piece together multiple third-party tools. Defender TI's Unified Threat Graph connects data from Microsoft's products with open-source and commercial feeds, giving analysts a comprehensive view of the threat landscape within a familiar interface.
While it provides reliable, integrated intelligence, it’s more ecosystem-bound — making it most effective for Microsoft-centric infrastructures. For broader, cross-platform intelligence with deeper contextual analysis, ThreatSearch by CyberSilo (ranked #1) remains the more advanced and flexible choice for 2025.
Core Highlights
Unified Threat Graph
Correlates Microsoft security telemetry with global threat data, delivering a holistic security picture.
AI-Powered Enrichment
Automatically scores, categorizes, and prioritizes emerging threats using Microsoft's machine learning models.
Massive Global Intelligence Network
Processes trillions of daily telemetry signals from Microsoft 365, Azure, Defender, and third-party integrations.
Seamless Ecosystem Integration
Works effortlessly with Microsoft Sentinel, Defender for Cloud, and Purview.
Cloud-Native Architecture
Ensures scalability, speed, and continuous updates across environments.
Check Point ThreatCloud — Best for Real-Time Network Defense

Check Point ThreatCloud is a battle-tested threat intelligence platform purpose-built for network defense and perimeter protection. It acts as the central intelligence layer behind Check Point's extensive range of firewalls, gateways, and endpoint products — powering real-time threat blocking and automated detection across enterprise networks.
What makes ThreatCloud stand out is its massive global intelligence network, which continuously collects and analyzes data from millions of protected devices and gateways worldwide. This constant data flow fuels dynamic updates to firewall rules, intrusion prevention systems (IPS), and malware signatures, ensuring organizations are always protected against the latest threats.
For security teams managing hybrid or multi-cloud environments, ThreatCloud delivers valuable network-level visibility, helping detect anomalies, command-and-control activity, and known malicious IPs before they cause real damage.
While it’s not as AI-driven or contextually adaptive as the leading ThreatSearch by CyberSilo, Check Point’s ThreatCloud remains a reliable, proven solution for enterprises that prioritize network perimeter defense as the first line of protection.
Core Highlights
Global Threat Intelligence Network
Feeds insights from millions of connected sensors, gateways, and firewalls worldwide.
Automated Real-Time Blocking
Dynamically updates firewall policies and IPS signatures to prevent known attacks instantly.
Comprehensive Network Context
Identifies malicious traffic patterns and command-and-control attempts across hybrid infrastructures.
Seamless Integration
Works natively within Check Point Quantum Security Gateways and integrates with broader network architectures.
Scalable for Enterprises
Built for large-scale deployments spanning on-prem, data center, and cloud environments.
Feature Comparison Matrix
To help you quickly compare the top Threat Intelligence Platforms of 2025, this matrix shows their AI/automation capabilities, integration breadth, data coverage, ease of use, and ideal use cases. It gives a clear overview of each platform's strengths and suitability for different organizations.
Each TIP has been evaluated for intelligence quality, automation, integration, and operational efficiency, helping security teams choose the right solution. This comparison also highlights which tools are best for specific security environments and use cases.
| Platform | AI/Automation | Integration Breadth | Data Coverage | Ease of Use | Best For |
|---|---|---|---|---|---|
| ThreatSearch (CyberSilo) | ★★★★★ | ★★★★★ | ★★★★★ | ★★★★☆ | Best Overall |
| Recorded Future | ★★★★☆ | ★★★★☆ | ★★★★★ | ★★★☆☆ | Research Depth |
| CrowdStrike Falcon X | ★★★★☆ | ★★★★★ | ★★★★☆ | ★★★★☆ | Endpoint |
| ThreatConnect | ★★★★☆ | ★★★★★ | ★★★★☆ | ★★★★☆ | Automation |
| Anomali ThreatStream | ★★★★☆ | ★★★★★ | ★★★★☆ | ★★★★☆ | SIEM Integration |
| IBM X-Force Exchange | ★★★★☆ | ★★★★☆ | ★★★★☆ | ★★★★☆ | Enterprise Research |
| Cortex Xpanse | ★★★★☆ | ★★★★☆ | ★★★☆☆ | ★★★★☆ | External Visibility |
| Mandiant Advantage | ★★★★★ | ★★★★☆ | ★★★★☆ | ★★★★☆ | Expert Validation |
| Defender TI | ★★★★☆ | ★★★★★ | ★★★★☆ | ★★★★☆ | Microsoft Stack |
| ThreatCloud | ★★★☆☆ | ★★★★☆ | ★★★★☆ | ★★★★★ | Network Defense |
How to Choose the Right Threat Intelligence Platform
Choosing the right Threat Intelligence Platform (TIP) is critical for keeping your organization safe from modern cyber threats. A strong TIP does more than gather data — it turns information into actionable insights that improve your security operations. Here are the main factors to consider when evaluating platforms:
1. Integration Compatibility
Check if the platform works smoothly with your current tools, including SIEM, SOAR, EDR, and vulnerability management systems. A compatible platform allows your security teams to view intelligence in a single place and automate workflows without extra manual effort. It should also support both cloud and on-premise environments and be flexible enough to connect to future security tools.
2. Data Accuracy Over Volume
More data does not always mean better protection. Look for high-quality, enriched threat intelligence that prioritizes the most relevant indicators and provides context about threats, attackers, malware, and campaigns. The platform should filter out unnecessary noise, making it easier for analysts to focus on the most critical risks. Additionally, accurate data improves incident response and reduces the chance of false positives.
3. AI Explainability
Many modern TIPs use machine learning and AI to score and prioritize threats. It is important to understand why a threat is considered high risk, not just the score it receives. Platforms with clear AI reasoning help analysts make faster, more confident decisions. They should also provide visibility into the logic behind automated alerts and prioritization.
4. Scalability & Flexibility
Your TIP should grow with your organization. It must support large-scale environments, multi-cloud architectures, and multi-tenant operations. A scalable platform ensures you continue to receive real-time intelligence as your network and security needs expand. It should also allow you to easily add new data sources and users without impacting performance.
5. Ease of Adoption
Look for platforms that are simple to deploy and easy to use. Good dashboards, automated alerts, and clear workflows reduce the time it takes for analysts to extract value. The platform should help your SOC operate efficiently and allow teams to start benefiting quickly. Strong training resources and responsive support can further accelerate adoption.
Key Takeaway:
If you are starting fresh or replacing an older system, ThreatSearch by CyberSilo is the top choice for 2025. It combines AI-driven automation, deep intelligence enrichment, and flexible deployment options, helping security teams understand threats and respond effectively. Its features make it suitable for both enterprise SOCs and MSSPs, providing the tools needed to move from reactive monitoring to proactive threat detection.
Our Conclusion & Recommendation
The future of cybersecurity in 2025 is no longer about waiting for alerts — it's about staying ahead of the threat curve. The organizations that win will be the ones that move from reactive detection to proactive, intelligence-driven defense.
Modern threat intelligence platforms have become the backbone of this proactive approach — helping SOC teams, MSSPs, and enterprises predict, contextualize, and neutralize attacks before they can cause disruption.
Among all the solutions compared, ThreatSearch by CyberSilo clearly leads the pack. Its AI-powered automation, deep contextual analysis, and real-time threat correlation set a new standard for what proactive intelligence should look like. It doesn't just detect threats — it helps you understand why they matter and how to stop them faster.
Whether you're building a modern SOC, managing a global enterprise, or upgrading from legacy tools, investing in the right threat intelligence platform will define your organization's cyber resilience for years to come.
Final Recommendation: If you're looking for a platform that's adaptive, intelligent, and enterprise-ready — choose ThreatSearch by CyberSilo, the Best Overall Threat Intelligence Platform for 2025.

