Today's businesses use more technology than ever before—cloud storage, remote work tools, smart devices, and many outside services. But here's the problem: each new tool or system can become a weak point that hackers can attack. Every forgotten app, outdated software, or poorly set up server could let cybercriminals break in.
The real challenge isn't just finding these weak spots—it's knowing which ones are the most dangerous and fixing them quickly before hackers find them first.
That's where threat exposure monitoring tools come in. These tools constantly watch your entire digital system, automatically finding security problems and telling you which ones need attention right away. They help you stay one step ahead of attackers instead of always playing catch-up.
But with so many options available, which tool should you choose?
In this comprehensive guide we have reviewed the top 10 threat exposure monitoring tools for 2026. Also we'll compare what makes each one special, what they're best at, and how they handle different security needs.
Whether you're protecting cloud data, company computers, or checking if your partners are secure, this guide will help you pick the right tool to keep your business safe. Let's get started!
TL;DR / Quick Recommendation
If you need a quick overview of the top threat exposure monitoring tools for 2026, here is a simple guide. These platforms help organizations identify vulnerabilities, monitor their attack surface, and prioritize risk remediation efficiently.
They provide continuous visibility into cloud, endpoint, and network assets, helping security teams stay ahead of emerging threats. Using these tools also supports cyber risk monitoring, threat intelligence integration, and compliance tracking, ensuring organizations can respond quickly and confidently to potential breaches.
| Tool | Key Strength | Ideal Use Case |
|---|---|---|
| Cybersilo | Centralized exposure management with automated risk remediation | Enterprise-wide visibility across cloud, endpoints, and IoT |
| Tenable One | Comprehensive vulnerability assessment and cloud exposure insights | Hybrid IT environments and large-scale enterprises |
| Qualys VMDR | Continuous vulnerability detection with automated patch workflow | Teams needing rapid detection and response |
These three tools are recommended for their strong integration capabilities, real-time risk prioritization, and automated workflows. Cybersilo provides complete visibility across all assets and simplifies attack surface monitoring for large organizations. Tenable One delivers detailed vulnerability management and cloud exposure insights for hybrid IT setups. Qualys VMDR ensures continuous scanning and actionable remediation guidance, helping teams address vulnerabilities before they are exploited.
For organizations managing endpoints, cloud workloads, or third-party risks, other solutions like CrowdStrike Falcon, UpGuard, and Cymulate can provide specialized monitoring and exposure management. The right tool should match your security goals, asset coverage, and automation needs. Implementing the correct platform ensures cyber exposure reduction, proactive threat monitoring, and stronger overall security posture.
Table of Contents
- What Makes a "Top" Threat Exposure Monitoring Tool — Our Evaluation Criteria
- Overview of Top 10 Threat Exposure Monitoring Tools — Expert Analysis & Ratings 2026
- Feature Comparison Matrix
- How to Choose the Right Threat Exposure Monitoring Tool
- Challenges & Pitfalls of Threat Exposure Monitoring Tools
- Our Conclusion & Recommendation
What Makes a "Top" Threat Exposure Monitoring Tool — Our Evaluation Criteria
Choosing the right threat exposure monitoring tool is more than just looking at a feature list. A top solution must meet key criteria that ensure it delivers maximum value. The right tool helps organizations identify vulnerabilities, track their attack surface, and prioritize risks efficiently. It also supports continuous monitoring, cyber risk management, and proactive exposure reduction. These factors ensure your organization can protect critical assets and maintain a strong security posture.
Coverage and Visibility
A top tool must provide complete visibility across all assets, including internet-facing systems, internal networks, cloud workloads, endpoints, and OT/IoT devices. It should also detect unmanaged assets, shadow IT, and forgotten cloud resources to ensure no risks are missed.
Comprehensive attack surface mapping allows teams to see all potential vulnerabilities and prioritize actions effectively. Strong coverage also helps organizations improve asset management, cyber exposure monitoring, and threat response planning. It ensures security teams have accurate, up-to-date information for decision-making.
Vulnerability Detection & Prioritization
Continuous vulnerability scanning and risk-based prioritization are essential for modern cybersecurity. Tools should provide actionable insights, correlate vulnerabilities with known exploits, and guide teams on which issues to fix first. Features like CVE tracking, automated patching workflows, and risk scoring make vulnerability management faster and more reliable.
Prioritizing critical threats first reduces exposure and helps prevent potential breaches. These features also strengthen proactive security measures and maintain a healthy vulnerability management lifecycle.
Threat Intelligence Integration
The best solutions integrate external cyber threat intelligence (CTI) feeds and use AI-driven analytics to connect global threats with an organization's internal assets. This enables predictive risk assessments, proactive monitoring, and automated alerts.
Combining threat intelligence with internal data helps identify high-risk areas faster and plan remediation effectively. It also improves decision-making, exposure assessment, and cyber risk monitoring. Teams can respond to emerging threats quickly and with confidence.
Ease of Deployment & Scalability
Deployment flexibility is important. Leading tools should support cloud-native, on-premises, and hybrid environments, integrate with SIEM and SOAR platforms, and scale easily for small teams or large enterprises. SaaS-based solutions offer faster setup and lower maintenance, while on-premises solutions may suit highly regulated organizations.
A flexible and scalable tool allows continuous monitoring, efficient resource management, and easy expansion as your infrastructure grows. It ensures consistent security coverage without adding operational burden.
Reporting & Compliance Support
A top monitoring tool should provide clear dashboards, executive reporting, and compliance support for frameworks like NIST, ISO 27001, GDPR, and CCPA. Automated reporting reduces manual effort and helps organizations stay audit-ready.
Effective reporting also allows teams to track risk trends, exposure levels, and mitigation progress. This information is critical for cyber risk management, executive decision-making, and regulatory compliance. It ensures stakeholders understand the organization's security posture clearly.
Overview of Top 10 Threat Exposure Monitoring Tools — Expert Analysis & Ratings 2026
Modern enterprises face an increasingly complex cyber landscape, with threats targeting endpoints, cloud workloads, IoT devices, and third-party systems. Selecting the right threat exposure monitoring tool is critical for identifying vulnerabilities, prioritizing risks, reducing attack surface exposure, and ensuring regulatory compliance.
The following is an expert-reviewed overview of the top 10 tools in 2026, highlighting features, integrations, ratings, and detailed enterprise-level use cases.
Cybersilo Threat Exposure Monitoring Tool — Best Overall

Overview:
The Cybersilo Threat Exposure Monitoring Tool is a comprehensive enterprise solution designed to provide centralized visibility, continuous monitoring, and automated remediation across cloud workloads,
endpoints, and IoT devices. Its AI-driven dashboards consolidate data into a single interface, helping security teams prioritize high-risk vulnerabilities and reduce overall cyber exposure efficiently. The platform supports
attack surface monitoring, continuous security validation, and proactive alerts, providing a unified approach to exposure management.
Security teams benefit from real-time risk scoring, integration with SIEM/SOAR tools, and compliance reporting for standards such as NIST, ISO 27001, GDPR, and CCPA. Its predictive analytics enable organizations to identify emerging threats and remediate vulnerabilities before they can be exploited. The tool also allows multi-tenant support and scalable deployment, making it suitable for distributed enterprises and hybrid cloud environments. Organizations can track trends, monitor exposure reduction progress, and generate executive-level reports, all from one platform.
Ideal Use Case:
Large enterprises managing hybrid clouds, remote endpoints, and IoT networks that require proactive risk management, automated remediation, and continuous visibility across all digital assets. Teams seeking real-time monitoring, exposure trend analysis, and compliance alignment will find this tool invaluable. It is particularly useful for organizations needing predictive threat insights and full attack surface monitoring.
Strengths:
Centralized visibility, AI-assisted remediation, seamless SIEM/SOAR integration, predictive threat analytics, continuous security validation
Tenable One

Overview:
Tenable One is an enterprise-grade vulnerability and exposure management solution that offers continuous scanning, cloud exposure mapping, and configuration assessment. The platform maps vulnerabilities
to business impact, helping teams prioritize remediation and maintain compliance with industry regulations. It provides dynamic dashboards, automated alerts, and integration with SIEM and IT workflows, delivering real-time
insights into attack surface risks.
The risk scoring engine enables security teams to focus on high-priority vulnerabilities first, reducing potential impact on operations. Tenable One also supports compliance automation, historical trend analysis, and executive reporting, which is essential for audit-ready environments. It is capable of monitoring complex hybrid environments, multi-cloud infrastructures, and distributed endpoints, giving teams a complete exposure overview. Security professionals can predict emerging threats, prioritize remediation effectively, and track exposure reduction over time.
Ideal Use Case:
Enterprises with complex hybrid IT environments and distributed assets that need deep vulnerability insights, automated compliance reporting, and real-time exposure management. Security teams seeking risk-based prioritization, actionable remediation guidance, and executive-level dashboards will benefit from Tenable One. It is also well-suited for organizations aiming to align security operations with business risk objectives.
Strengths:
Broad coverage, risk-based prioritization, automated compliance, advanced threat correlation, actionable executive reporting
Qualys VMDR

Overview:
The Qualys VMDR Threat Exposure Monitoring Tool provides continuous vulnerability detection, automated patching, and integrated threat intelligence, helping organizations address risks before they
can be exploited. Its dashboards offer real-time visibility into endpoints, cloud workloads, and network assets, allowing teams to monitor exposure trends continuously.
Integration with IT workflows and SIEM platforms streamlines vulnerability management, while risk scoring and remediation guidance help teams focus on high-impact vulnerabilities first. The platform supports compliance reporting, trend analysis, and executive dashboards, enabling organizations to demonstrate cybersecurity effectiveness. VMDR also provides predictive analytics, automated alerts, and exposure prioritization, allowing teams to take proactive measures against emerging threats.
Ideal Use Case:
Organizations requiring real-time detection and automated remediation across hybrid IT environments. VMDR is highly effective for teams managing cloud, endpoints, and network infrastructure, especially those that need actionable insights for continuous security validation and regulatory compliance. Security professionals can analyze exposure trends, prioritize high-risk vulnerabilities, and optimize remediation workflows.
Strengths:
Continuous scanning, integrated threat intelligence, automated remediation, risk-based prioritization, predictive analytics
CrowdStrike Falcon Exposure Management

Overview:
The CrowdStrike Falcon Exposure Management Tool provides AI-driven monitoring for endpoints and cloud workloads, delivering real-time threat detection, automated risk prioritization, and continuous
exposure insights. Its lightweight agents allow teams to track vulnerabilities and detect anomalous behaviors without impacting performance. The platform integrates with SIEM solutions, ticketing systems, and other security
workflows, enabling a unified operational view.
CrowdStrike Falcon includes dynamic dashboards, automated alerts, and trend tracking, allowing organizations to visualize high-risk assets and reduce overall attack surface exposure. It is particularly effective in distributed, hybrid environments, where endpoints, cloud services, and IoT devices require continuous oversight. The AI-driven analytics provide predictive insights, helping teams proactively mitigate emerging threats. Additionally, Falcon supports scalable deployments, executive reporting, and compliance management, ensuring security operations remain efficient and aligned with organizational goals.
Ideal Use Case:
Enterprises prioritizing endpoint and cloud security, especially in hybrid and distributed IT environments. Security teams seeking real-time monitoring, AI-assisted risk scoring, and automated exposure remediation will benefit most. The tool is also ideal for organizations needing proactive exposure management and predictive threat insights.
Strengths:
AI-driven analytics, continuous endpoint and cloud monitoring, predictive threat prioritization, integration with SIEM, real-time dashboards
Rapid7 InsightVM / Exposure Command

Overview:
The Rapid7 InsightVM / Exposure Command Tool is designed to help security teams focus on actionable vulnerabilities using risk-based prioritization. Its dynamic dashboards provide real-time exposure
insights, highlighting high-priority vulnerabilities across endpoints, networks, and cloud workloads. Integration with SIEM and IT ticketing systems streamlines remediation workflows and accelerates response times.
InsightVM includes automated reporting, trend tracking, and predictive risk analytics, enabling teams to anticipate potential threats and reduce overall cyber exposure. Security teams can track remediation progress, measure exposure reduction, and ensure compliance with internal and external standards. It also provides customizable dashboards and alerts, allowing organizations to tailor monitoring to their unique attack surfaces.
Ideal Use Case:
Security teams needing targeted insights for high-risk vulnerabilities in distributed or hybrid IT environments. It is particularly useful for organizations aiming to prioritize remediation effectively, integrate exposure data into IT workflows, and maintain continuous visibility across endpoints, networks, and cloud assets.
Strengths:
Risk-based prioritization, dynamic dashboards, actionable vulnerability insights, integration with IT workflows, predictive analytics
Microsoft Defender External Attack Surface Management
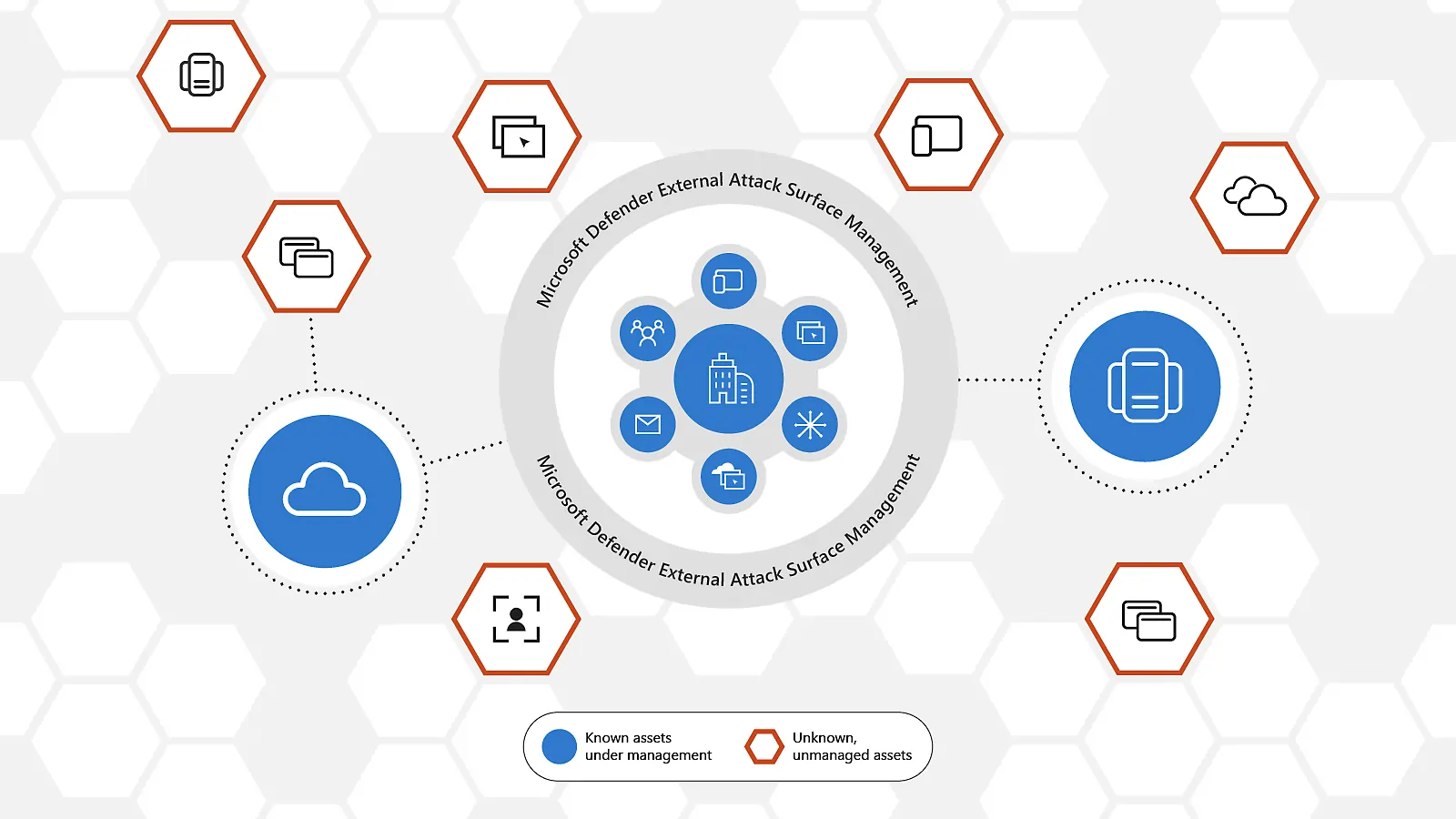
Overview:
The Microsoft Defender External Attack Surface Management (EASM) Tool focuses on identifying and monitoring internet-facing vulnerabilities across cloud and on-premises assets. Its cloud-native architecture
simplifies scanning and detection, providing continuous visibility into the organization's exposed assets. The platform integrates seamlessly with Azure, Microsoft 365, and other Microsoft ecosystem tools, enabling consolidated
management and real-time risk monitoring.
Defender EASM offers automated alerts, exposure dashboards, and compliance tracking for internet-facing systems. It helps teams identify shadow IT, monitor external threats, and prioritize remediation to reduce potential attack vectors. Security teams can also analyze trends over time, track remediation efficiency, and generate executive reports to support strategic decision-making. Its scalable cloud-native deployment allows rapid adoption for organizations of all sizes.
Ideal Use Case:
Enterprises heavily invested in Microsoft cloud environments that need external attack surface monitoring and proactive vulnerability detection. It is ideal for organizations seeking continuous monitoring, automated alerts, and integration with Microsoft security and productivity tools.
Strengths:
Cloud-native scanning, integration with Microsoft ecosystem, continuous exposure visibility, automated alerts, executive dashboards
CyCognito
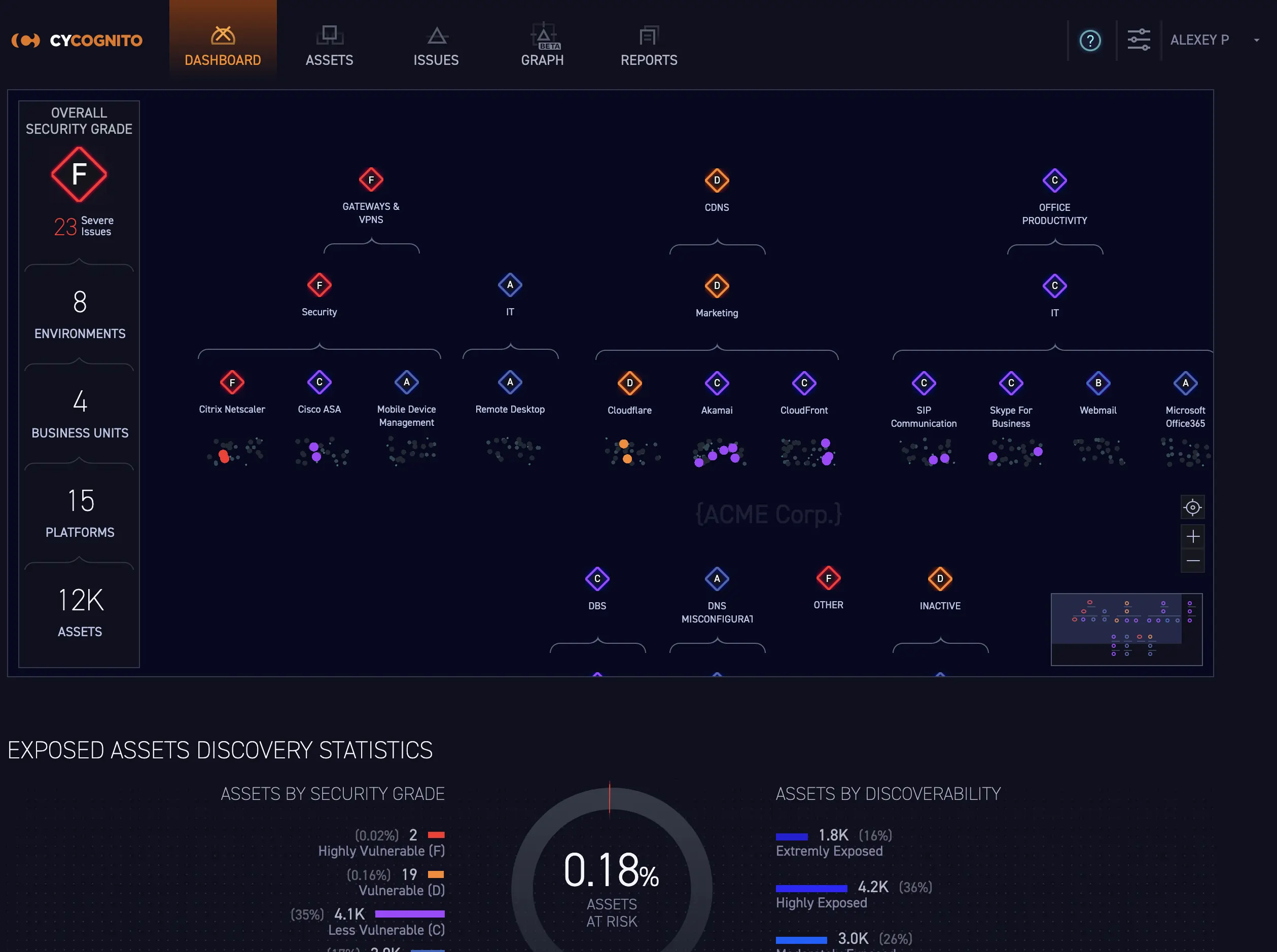
Overview:
The CyCognito Threat Exposure Monitoring Tool specializes in proactive attack surface discovery. It identifies unmanaged assets, shadow IT, and hidden vulnerabilities across cloud, endpoints, and
networks before attackers can exploit them. The platform provides comprehensive dashboards, automated alerts, and integration with SIEM platforms, enabling security teams to continuously monitor and reduce exposure.
CyCognito also provides risk scoring, exposure trend analytics, and remediation guidance, helping organizations prioritize high-risk assets effectively. Teams can track historical exposure data, generate compliance-ready reports, and integrate insights into broader security operations. Its proactive monitoring approach allows organizations to maintain visibility across both managed and unmanaged assets, ensuring no critical gaps are overlooked.
Ideal Use Case:
Organizations needing full visibility of both managed and unmanaged assets, particularly those with complex IT environments or hybrid cloud architectures. Security teams aiming to proactively identify vulnerabilities, reduce attack surface, and integrate exposure data into security operations will find CyCognito highly effective.
Strengths:
Full attack surface visibility, proactive monitoring, automated alerts, SIEM integration, predictive exposure analytics
UpGuard

Overview:
The UpGuard Threat Exposure Monitoring Tool focuses on third-party and supply chain risk management, continuously monitoring vendors, contractors, and external partners. It provides security ratings,
breach detection alerts, and exposure dashboards, giving teams actionable insights into external cyber risks. The platform supports integration with IT and security workflows, enabling seamless monitoring alongside internal
security operations.
UpGuard also includes trend analysis, risk scoring, and reporting tools, allowing organizations to track exposure over time and measure the effectiveness of mitigation strategies. Teams can identify risky vendors, monitor compliance with contractual security requirements, and generate reports for audit purposes. Its continuous monitoring capabilities ensure that third-party risks are proactively addressed, reducing the likelihood of supply chain attacks.
Ideal Use Case:
Companies concerned with third-party risk management and supply chain security, especially those with large vendor networks and critical dependencies on external partners. Security teams needing continuous monitoring, automated alerts, and actionable insights into vendor exposure will benefit most.
Strengths:
Continuous vendor monitoring, supply chain risk scoring, breach alerts, integration with security workflows, exposure trend analysis
Recorded Future

Overview:
The Recorded Future Threat Exposure Monitoring Tool integrates real-time threat intelligence with predictive analytics, correlating external threats with internal vulnerabilities. This allows teams
to identify emerging risks, prioritize remediation, and reduce overall exposure proactively. Dashboards provide continuous monitoring, automated alerts, and actionable insights for IT and security teams.
Recorded Future also supports integration with SIEM, IT workflows, and vulnerability management platforms, ensuring efficient operational use and unified visibility. Teams can track exposure trends, analyze potential threat vectors, and generate executive reports for compliance and strategic planning. Its predictive analytics enable proactive threat mitigation, exposure reduction, and informed decision-making.
Ideal Use Case:
Enterprises wanting to integrate threat intelligence with vulnerability and exposure management workflows, particularly large organizations managing distributed IT infrastructures and hybrid cloud environments. Security teams seeking predictive analytics, actionable alerts, and continuous exposure monitoring will benefit most.
Strengths:
Threat intelligence integration, predictive analytics, continuous monitoring, automated alerts, actionable exposure insights
Cymulate
Overview:
The Cymulate Threat Exposure Monitoring Tool provides continuous security validation and simulated attack testing across endpoints, cloud, and network assets. Its automated attack simulations, phishing
campaigns, and breach & attack emulations allow organizations to identify weak points and validate security controls proactively. Dashboards deliver actionable insights, real-time alerts, and exposure trend analysis, helping
teams optimize remediation efforts.
Cymulate supports integration with SIEM and security workflows, enabling organizations to incorporate exposure testing into broader security operations. Security teams can track historical trends, measure control effectiveness, and continuously test defenses. The platform also provides reporting for compliance and executive visibility, ensuring organizations can demonstrate risk reduction and proactive threat management.
Ideal Use Case:
Security teams seeking continuous testing of security controls and exposure reduction through simulated attacks. It is ideal for organizations wanting to proactively identify vulnerabilities, validate defenses, and maintain continuous security validation across complex IT environments.
Strengths:
Continuous security validation, simulated attack testing, actionable insights, integration with SIEM, proactive exposure reduction
Feature Comparison Matrix
This matrix provides a side-by-side comparison of the top threat exposure monitoring tools, highlighting their asset coverage, vulnerability detection capabilities, threat intelligence integration, automation levels, reporting features, and pricing models.
| Tool Name | Asset Coverage | Vulnerability Detection | Threat Intel Integration | Automation | Reporting & Compliance | Pricing/Deployment |
|---|---|---|---|---|---|---|
| Cybersilo | Cloud, Endpoint, IoT | Enterprise | ||||
| Tenable One | Cloud, Hybrid | Mid-High | ||||
| Qualys VMDR | Cloud, Endpoint | Mid | ||||
| CrowdStrike Falcon | Endpoint, Cloud | Mid-High | ||||
| Rapid7 InsightVM | Cloud, Endpoint | Mid | ||||
| Microsoft Defender EASM | Cloud, Internet-Facing | Mid | ||||
| CyCognito | Cloud, Endpoint, OT | Mid-High | ||||
| UpGuard | Vendor/Supply Chain | Mid | ||||
| Recorded Future | Cloud, Endpoint | High | ||||
| Cymulate | Cloud, Endpoint | Mid |
Why This Comparison Matters
- Identify tools with comprehensive asset coverage for your specific environment
- Compare automation levels for operational efficiency and reduced manual effort
- Understand reporting capabilities for audit readiness and compliance requirements
- Evaluate threat intelligence integration for proactive threat detection
- Select the right pricing model based on organizational budget and needs
How to Choose the Right Threat Exposure Monitoring Tool
Selecting the right threat exposure monitoring tool is essential for organizations aiming to identify vulnerabilities, prioritize risks, and reduce cyber exposure. A carefully chosen tool ensures teams can monitor all digital assets, detect threats early, and maintain compliance with industry standards. To make an informed decision, organizations should follow a structured approach.
Understand Your Attack Surface Needs
Start by identifying all critical assets that require monitoring, including internet-facing systems, internal networks, endpoints, cloud workloads, and OT/IoT devices. Conducting a comprehensive attack surface inventory ensures no asset is overlooked and allows teams to focus on high-risk areas first. Include third-party integrations, shadow IT, and remote devices in your assessment to achieve complete visibility.
Tools that provide continuous discovery and attack surface mapping help security teams track unmanaged assets and maintain up-to-date exposure information. Fully understanding your attack surface allows organizations to prioritize monitoring and optimize cybersecurity resources effectively.
Ideal Use Case: Organizations with complex hybrid environments, distributed endpoints, and multiple cloud workloads that need complete visibility of all assets, real-time monitoring, and proactive exposure management.
Align Tool Features With Security Goals
Ensure the tool's features match your security objectives, such as vulnerability scanning, threat intelligence integration, automated risk scoring, and compliance reporting. The right solution supports operational priorities, whether that's continuous endpoint monitoring, cloud visibility, or supply chain risk assessment.
Tools offering actionable dashboards, predictive analytics, and real-time alerts help teams identify critical vulnerabilities and remediate them faster. Choosing a solution aligned with your goals ensures maximum efficiency, better threat prioritization, and improved security outcomes.
Ideal Use Case: Security teams aiming for proactive risk management, automated vulnerability remediation, and integration of exposure insights into daily operations.
Evaluate Deployment and Scalability
Consider how the tool fits into your current IT infrastructure and whether it can scale as your organization grows. Look at cloud-native, on-premises, or hybrid deployment options, along with API integrations, multi-site support, and multi-tenant capabilities.
Scalable solutions allow teams to add new endpoints, cloud workloads, and network devices seamlessly. Ensure the tool integrates with existing SIEM/SOAR systems, streamlining workflows and maintaining operational efficiency. Scalable, flexible solutions help organizations adapt to changing IT environments and future growth without disruption.
Ideal Use Case: Organizations that plan to expand IT infrastructure, adopt hybrid cloud strategies, or scale security operations across multiple sites.
Assess Cost vs. Value and ROI
Compare pricing models such as subscription tiers, per-asset licenses, or enterprise packages. Focus on the long-term value and ROI, including reduced remediation efforts, faster detection of vulnerabilities, and prevention of potential breaches.
Tools with automated monitoring, exposure dashboards, and predictive threat analytics save teams significant time and operational effort. Evaluating cost versus value ensures that the organization invests in a solution that strengthens cybersecurity posture while optimizing budget efficiency.
Ideal Use Case: Security leaders seeking a solution that balances cost with measurable impact on exposure reduction, operational efficiency, and compliance management.
Vendor Support and Ecosystem
Strong vendor support ensures smooth deployment, ongoing updates, and effective use of all features. Evaluate customer support quality, response times, and community resources, such as forums, knowledge bases, or training programs.
Also, check how well the tool integrates into your existing ecosystem, including SIEM, SOAR, IT workflows, and other security platforms. Vendors with robust support and integration capabilities help organizations maximize the value of the tool, maintain continuous monitoring, and stay ahead of emerging threats. Reliable vendor support ensures teams can implement best practices and address challenges efficiently.
Ideal Use Case: Organizations requiring strong vendor assistance, seamless integration with existing security tools, and long-term support for proactive exposure management.
Challenges & Pitfalls of Threat Exposure Monitoring Tools
Even the most advanced threat exposure monitoring tools face challenges that can affect efficiency and effectiveness. Understanding these challenges allows security teams to plan better, optimize tool usage, and maintain strong cybersecurity posture.
False Positives and Alert Fatigue
Excessive alerts or false positives can overwhelm security teams, making it difficult to focus on the most critical vulnerabilities. This can slow down incident response and risk remediation, leaving organizations more exposed. Tools with risk scoring, intelligent alert filtering, and predictive analytics can prioritize high-risk issues and reduce unnecessary noise.
Regular tuning of dashboards and alert thresholds allows teams to focus on actionable threats and critical exposures. Continuous monitoring combined with automated prioritization ensures that teams respond efficiently to vulnerabilities, improving overall cybersecurity effectiveness.
Ideal Use Case: Security teams needing efficient alert management and automated risk prioritization to reduce vulnerability management overhead and maintain continuous exposure awareness.
Integration Difficulties
Many tools can face challenges when integrating with existing security infrastructure, such as SIEM, SOAR, IT workflows, or endpoint management systems. Poor integration can lead to fragmented monitoring, delayed response, and incomplete visibility across the attack surface.
Selecting tools with API support, standardized data formats, and prebuilt integrations ensures seamless operation and unified monitoring. Properly integrated tools allow teams to correlate alerts, automate remediation workflows, and maintain a comprehensive view of vulnerabilities. Integration also ensures continuous exposure detection and smooth communication across all security platforms, enhancing operational efficiency.
Ideal Use Case: Organizations needing fully integrated monitoring tools that work with existing security systems and IT workflows for unified risk visibility and vulnerability management.
Scalability Issues
Large enterprises or organizations with complex IT environments may encounter scalability challenges. Adding endpoints, cloud workloads, and IoT/OT devices can require more resources or licenses if the tool cannot scale efficiently. Solutions with cloud-native architecture, automated asset discovery, and multi-tenancy can handle growing environments without compromising performance.
Scalable tools ensure that all assets are continuously monitored and that security teams maintain visibility as the organization expands. Planning for scalability allows organizations to adapt to IT growth, support multi-site operations, and prevent exposure gaps effectively.
Ideal Use Case: Companies with rapidly growing infrastructures, multiple cloud environments, or distributed endpoints that require scalable, continuous exposure monitoring.
Resource Requirements
Continuous monitoring, vulnerability scanning, and remediation demand significant team effort. Security teams may spend considerable time reviewing alerts, investigating exposure, and implementing remediation steps. Tools with automation, predictive analytics, and actionable dashboards reduce manual work and allow teams to focus on high-priority risks.
Efficient resource planning ensures monitoring remains effective without overburdening staff, even in environments with large asset counts or frequent changes. Leveraging workflow automation and integrated reporting helps teams maintain consistent vulnerability management and proactive risk reduction.
Ideal Use Case: Organizations looking for resource-efficient monitoring solutions that combine automation, predictive insights, and actionable reporting to optimize security operations.
Limitations of Continuous Scanning
Even with 24/7 monitoring, shadow IT, unmanaged devices, and third-party systems may remain unmonitored. These blind spots create potential gaps in attack surface visibility and exposure detection. Tools that support full attack surface discovery, external scanning, and automated asset updates can help reduce these gaps.
Regular audits, combined with integration of threat intelligence feeds, ensure teams maintain comprehensive visibility and reduce exposure risk. Continuous improvement and proactive identification of hidden assets allow organizations to strengthen defenses and stay ahead of emerging threats.
Ideal Use Case: Security teams requiring comprehensive asset visibility, including managed, unmanaged, and third-party systems, to proactively reduce attack surface risk.
While threat exposure monitoring tools are essential for modern cybersecurity, organizations must address security monitoring challenges, vulnerability management pitfalls, and exposure detection limitations. By tackling false positives, integration challenges, scalability, resource demands, and scanning blind spots, teams can maximize tool effectiveness, maintain continuous visibility, and enhance overall cybersecurity posture. Proper planning, automation, and integration allow teams to proactively manage risks, streamline vulnerability remediation, and maintain full exposure awareness across all assets.
Conclusion
In conclusion, yes—getting the right threat exposure monitoring tool is necessary to keep your business safe from cyber attacks. Without constant monitoring, hackers can easily find and exploit weak spots in your systems, cloud storage, and devices.
This guide reviewed ten powerful tools that help protect your business. Among all options, Cybersilo's Threat Exposure Monitoring Tool stands out as the best choice—it gives you complete visibility across all your systems and fixes problems automatically. Other solid options include Tenable One for complex IT setups, Qualys VMDR for quick threat detection, CrowdStrike Falcon for smart monitoring, UpGuard for vendor security, and Cymulate for testing your defenses.
Picking the right tool means knowing what you need to protect, choosing features that match your goals, and making sure it works with your current systems. You should also be prepared for challenges like too many alerts and keeping everything running smoothly as your business grows.
Ready to secure your business from cyber threats?
Start by understanding what assets you need to protect, then implement a monitoring solution that gives you full visibility and fixes vulnerabilities automatically.
Cybersilo's Threat Exposure Monitoring Tool offers everything you need in one platform—from real-time alerts to automated remediation. Don't leave your business exposed to attackers. Take action today and build stronger defenses before it's too late.
