Threat Search – Actionable Threat Intelligence for SOC
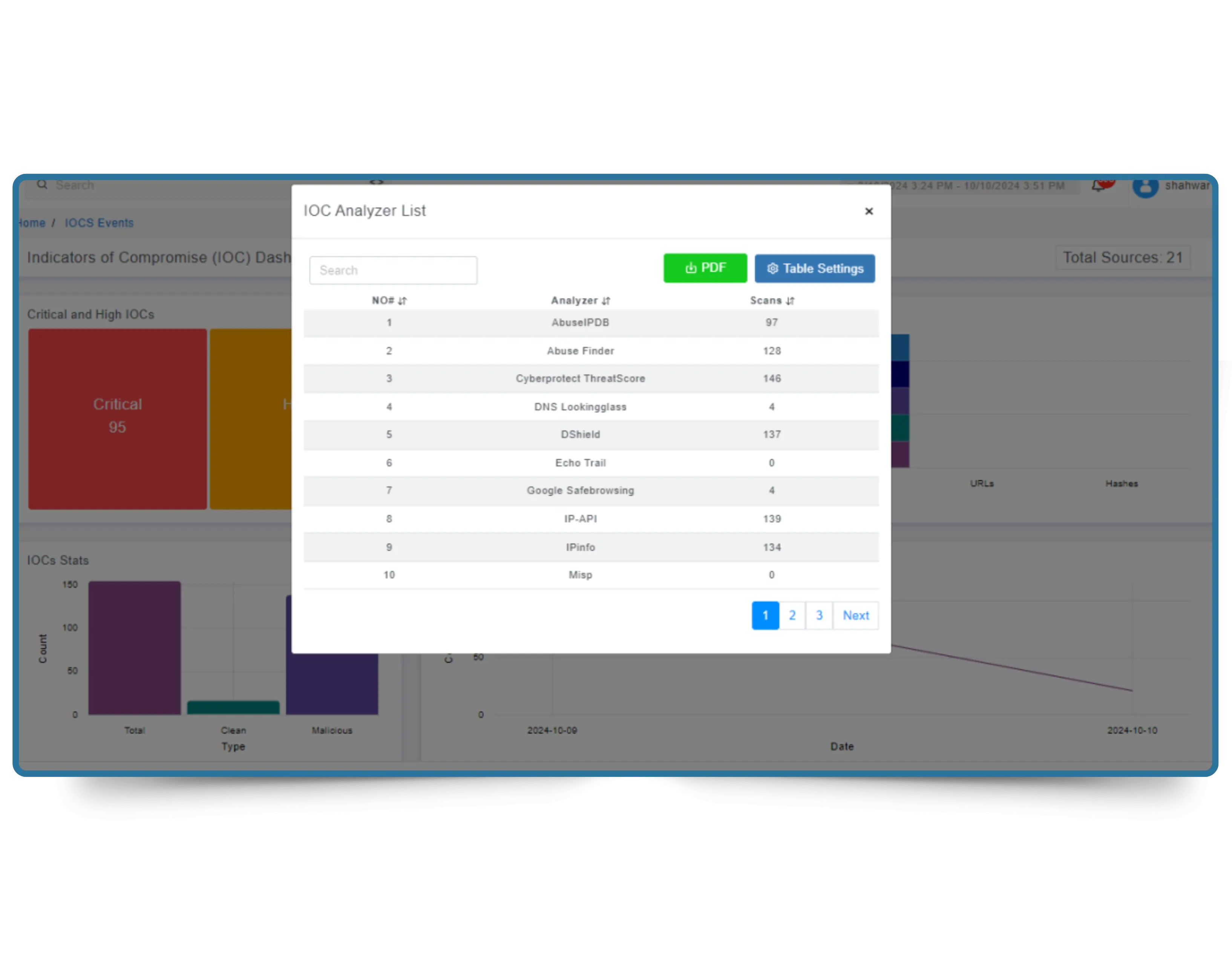
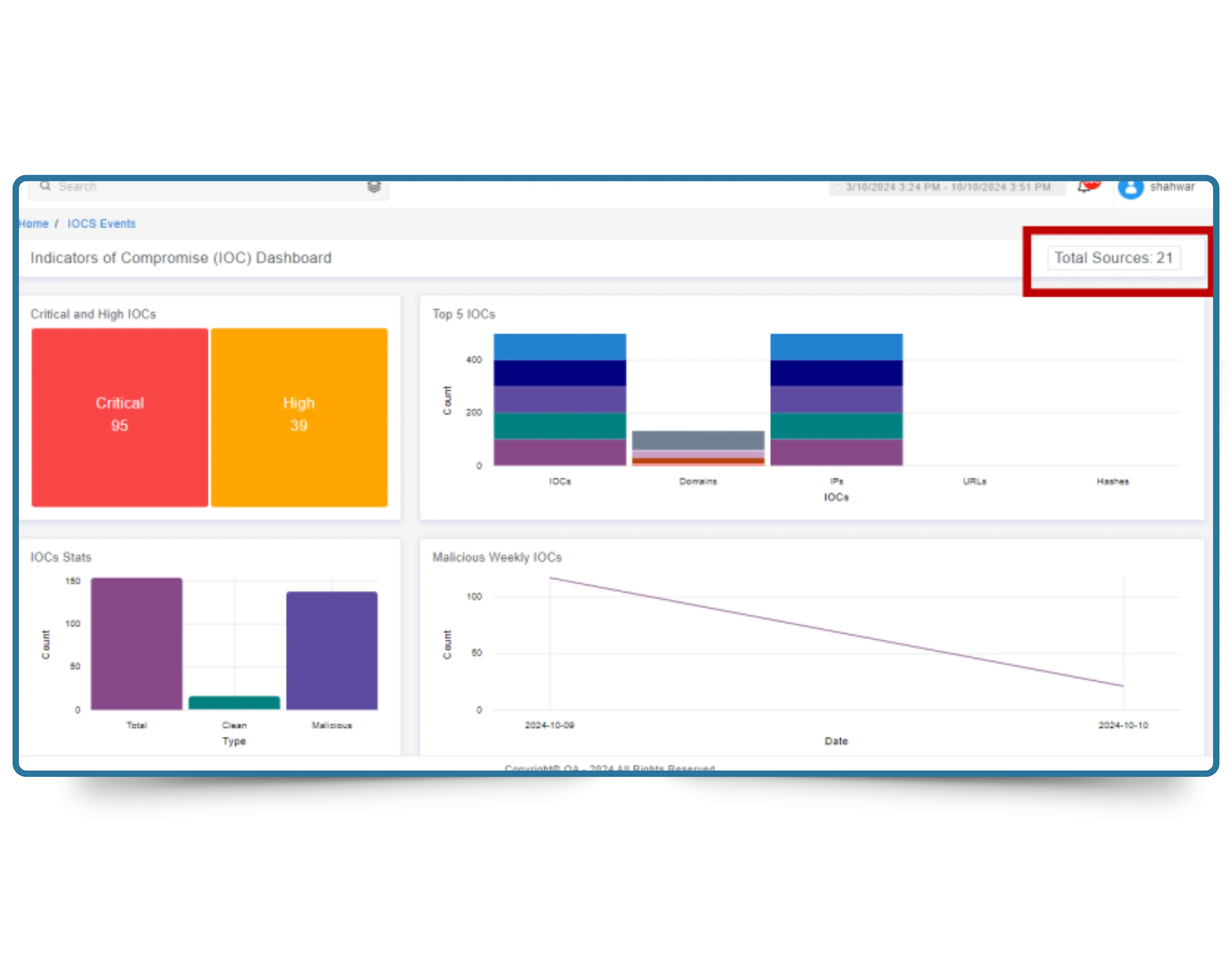
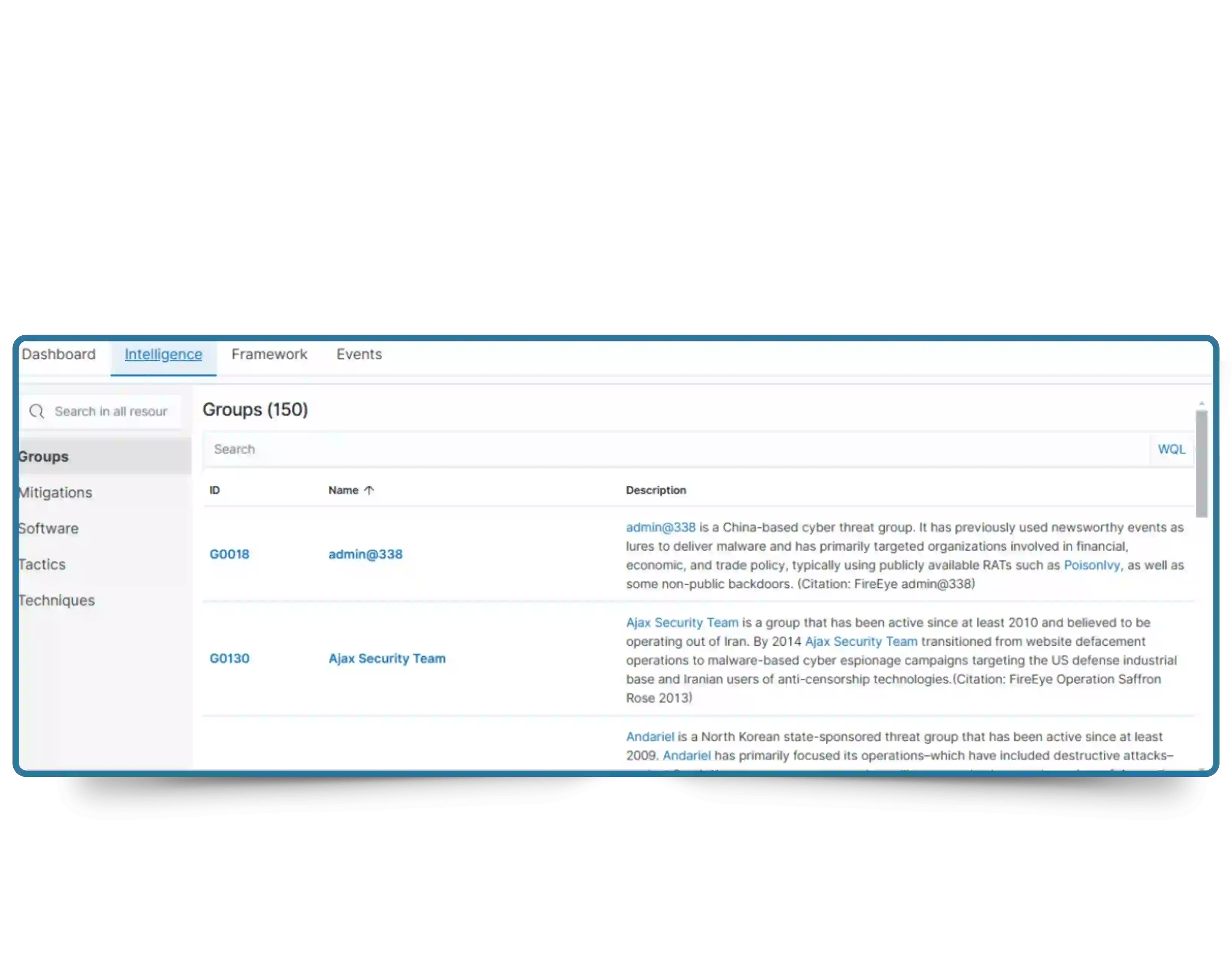
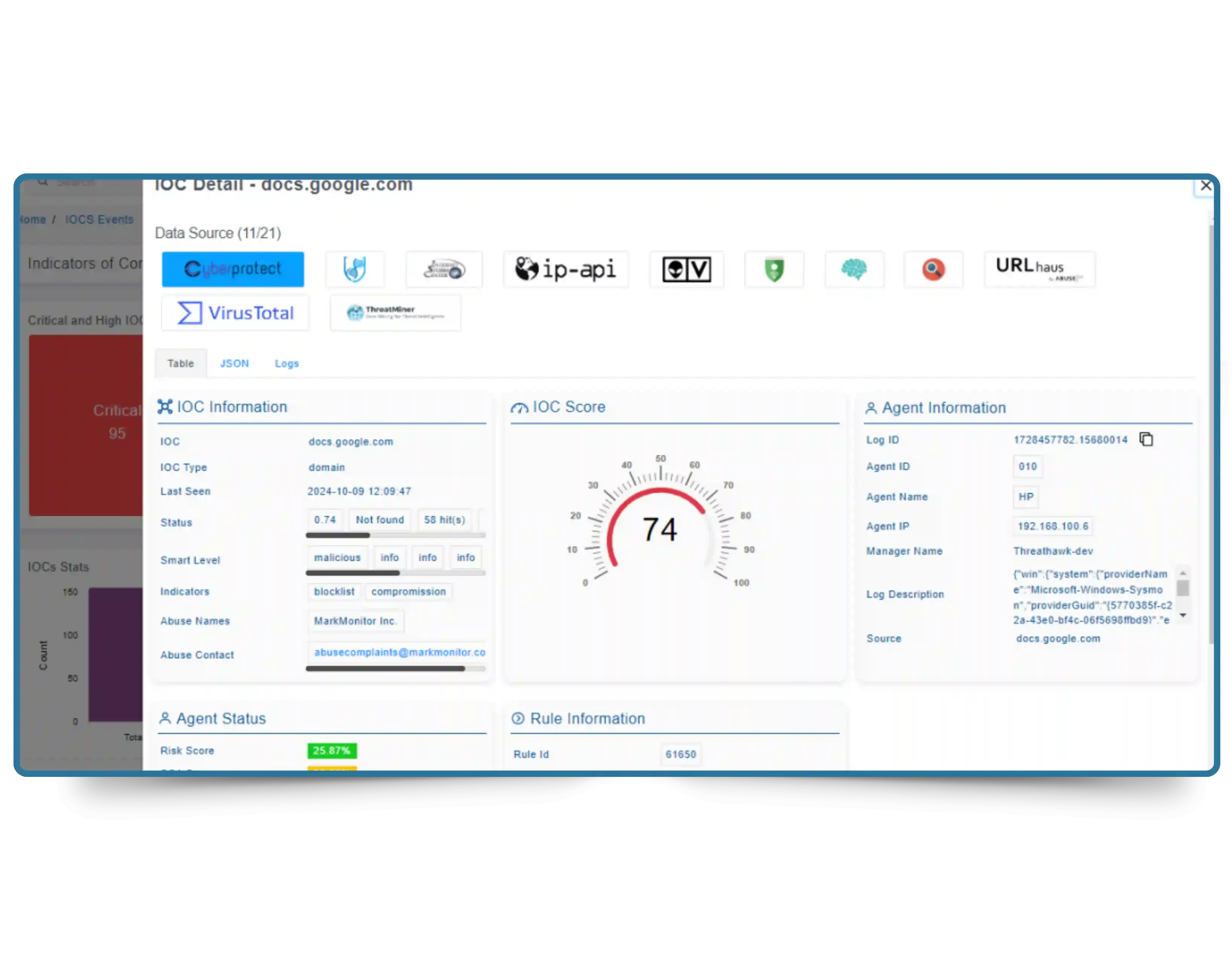
Stay ahead of evolving cyber threats with Cyber Silo's Threat Search, your always-on cyber threat intelligence platform. Real-time engine for collecting, enriching, and analyzing threat data, empowering security teams with smarter malware detection, IP threat search, and early vulnerability discovery.
Every second your delay leaves your environment exposed. Threat actors don't wait, why should your defenses?