Threat Exposure Monitoring (TEM)
Proactively manage your cyber attack surface with real-time vulnerability management across endpoints, network devices, and cloud assets, before attackers can exploit security holes.
Cyber Silo's Threat Exposure Monitoring (TEM) tool is an advanced vulnerability management solution that continuously scans your infrastructure to detect, classify, and enrich vulnerabilities with actionable threat intelligence. TEM helps reduce your exposure to evolving cyber threats and strengthens your cybersecurity posture.
Perform continuous scanning using agent-based and agentless methods. TEM covers your entire digital landscape including on-prem, hybrid, and cloud assets to help reduce attack surface exposure.
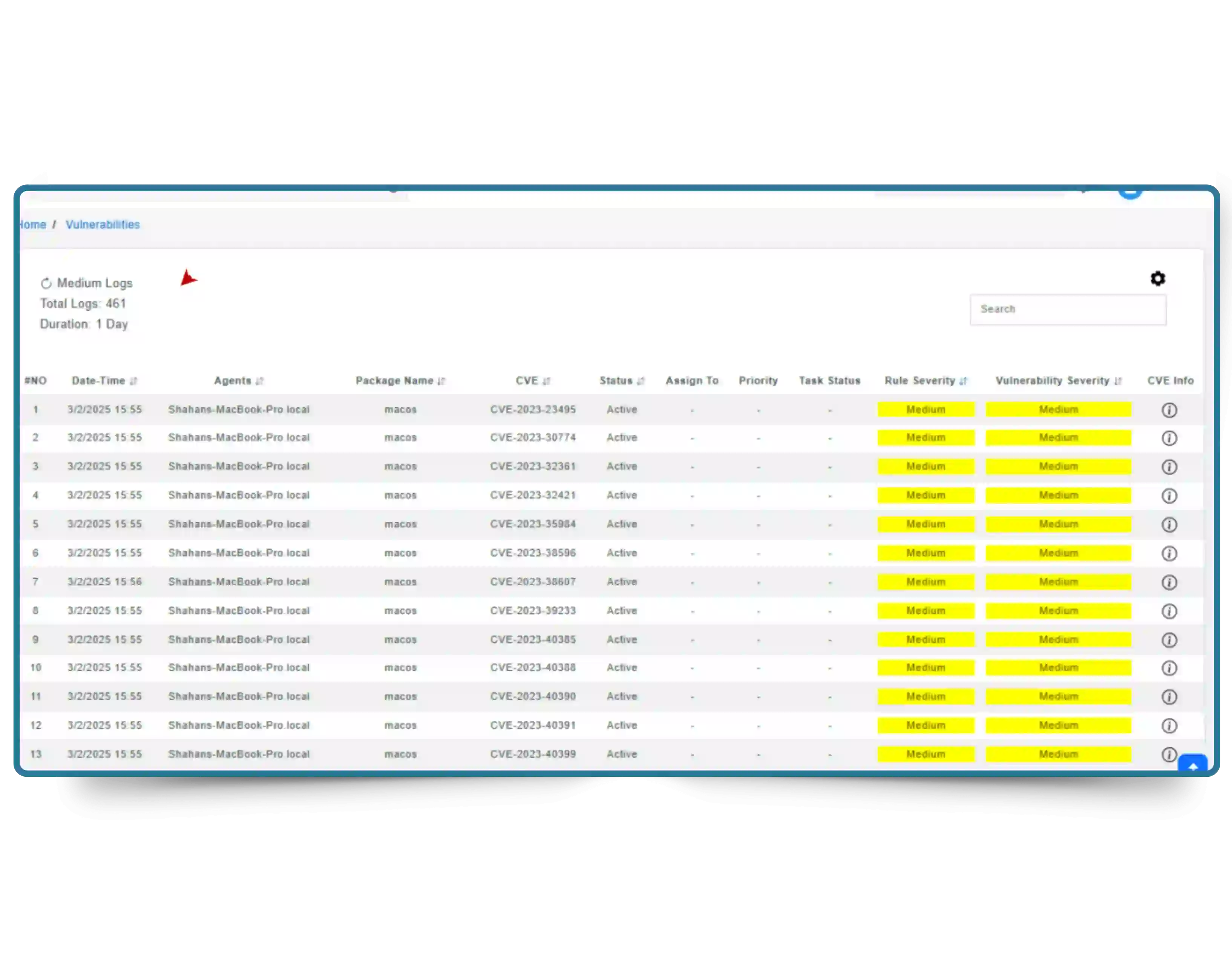
Gain visibility into security vulnerabilities with severity-based CVSS scoring, references, and mapped compliance. Quickly filter by risk level, affected assets, CVE ID, or remediation status.
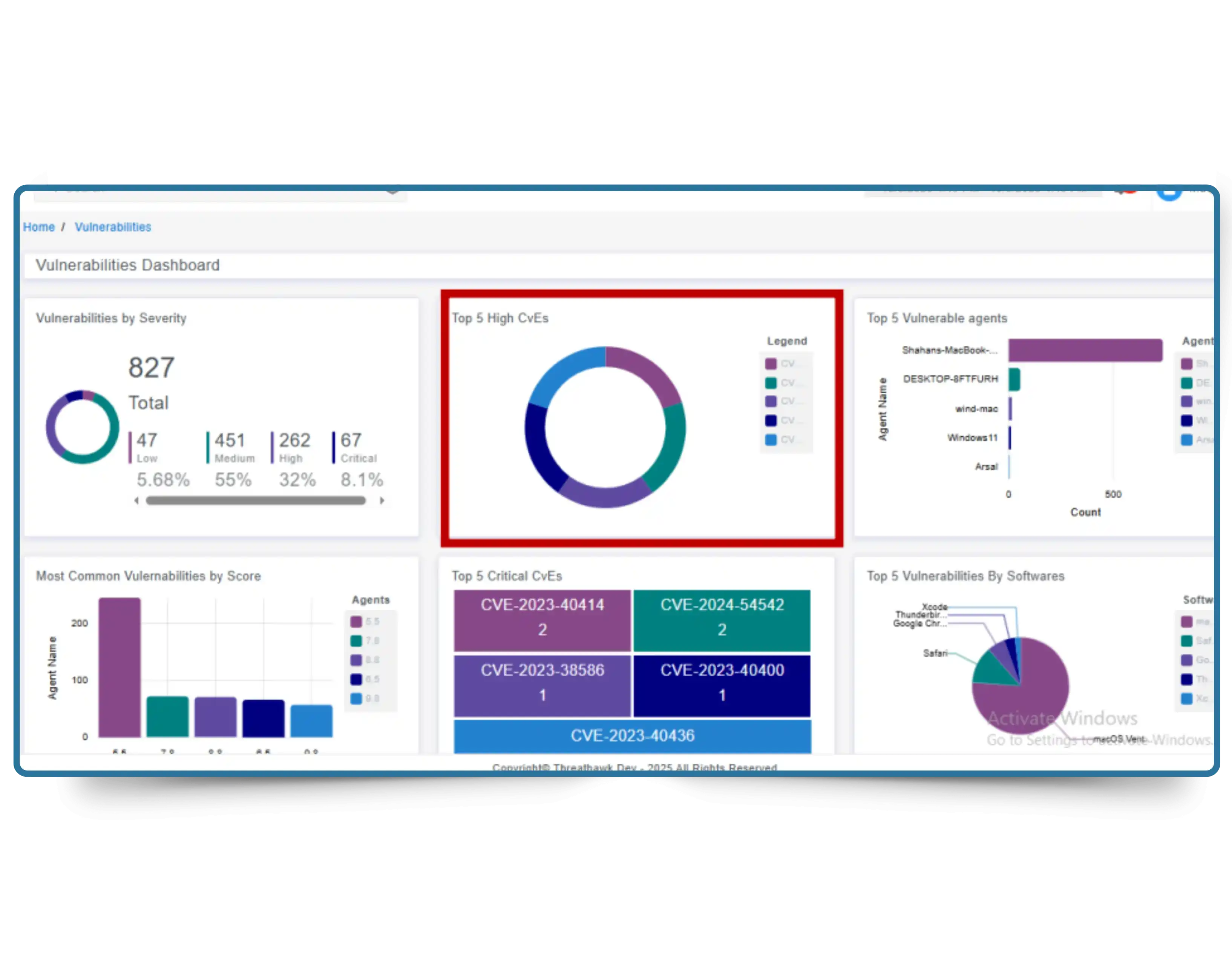
Our dashboards give real-time insights into your vulnerability data. Visualize:
1. Top 5 High-Risk CVEs
2. Most Impacted Software
3. Open vs Resolved Issues
4. Security posture across your network and
cloud infrastructure.
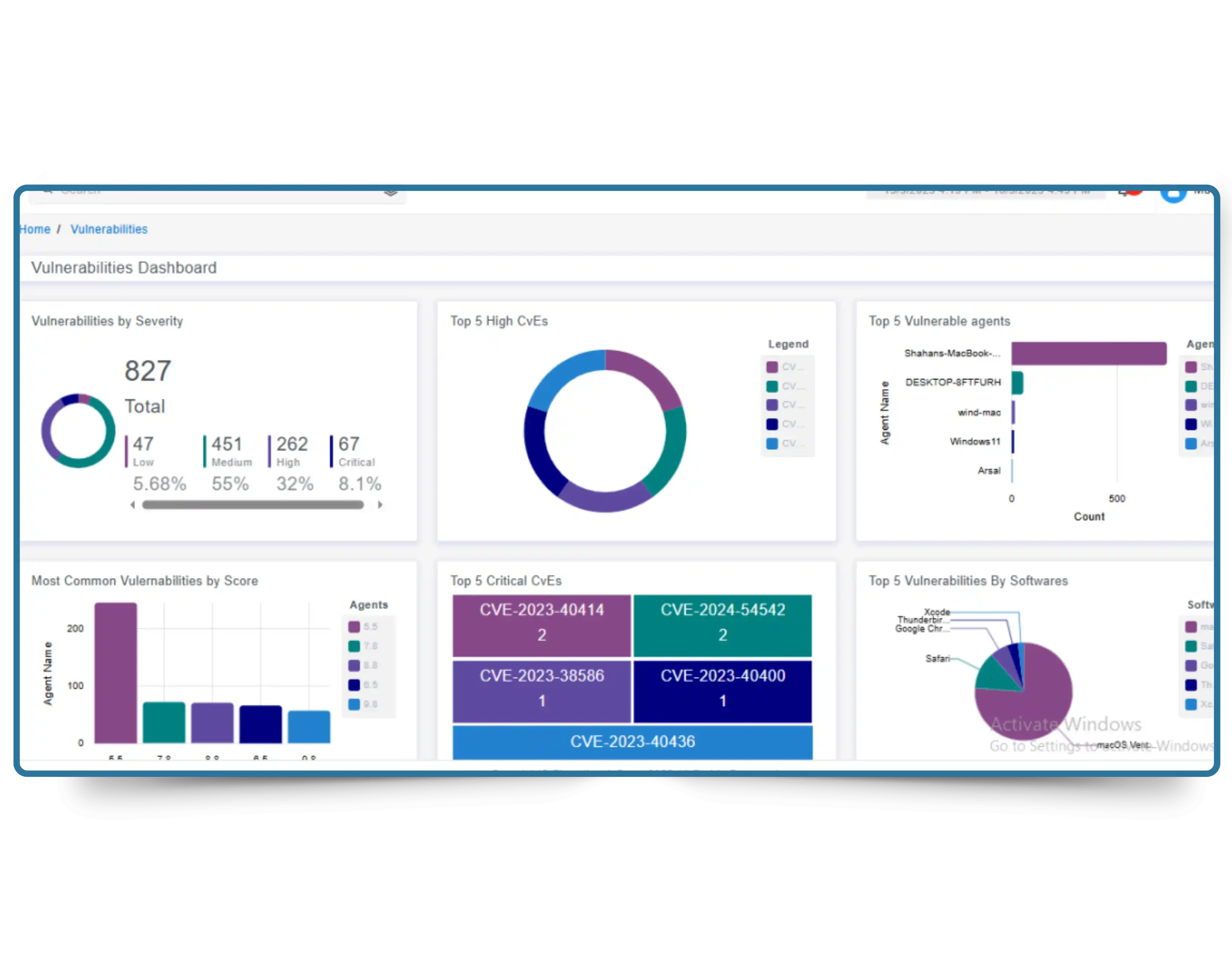
Real-time, always-on detection across your entire infrastructure cloud, on-prem, and hybrid. TEM continuously monitors all assets to uncover vulnerabilities before exploitation. Gain 50% faster detection, 40% reduced attack surface risk, 45% better patch management, and 35% stronger compliance with standards like ISO 27001 and NIST.
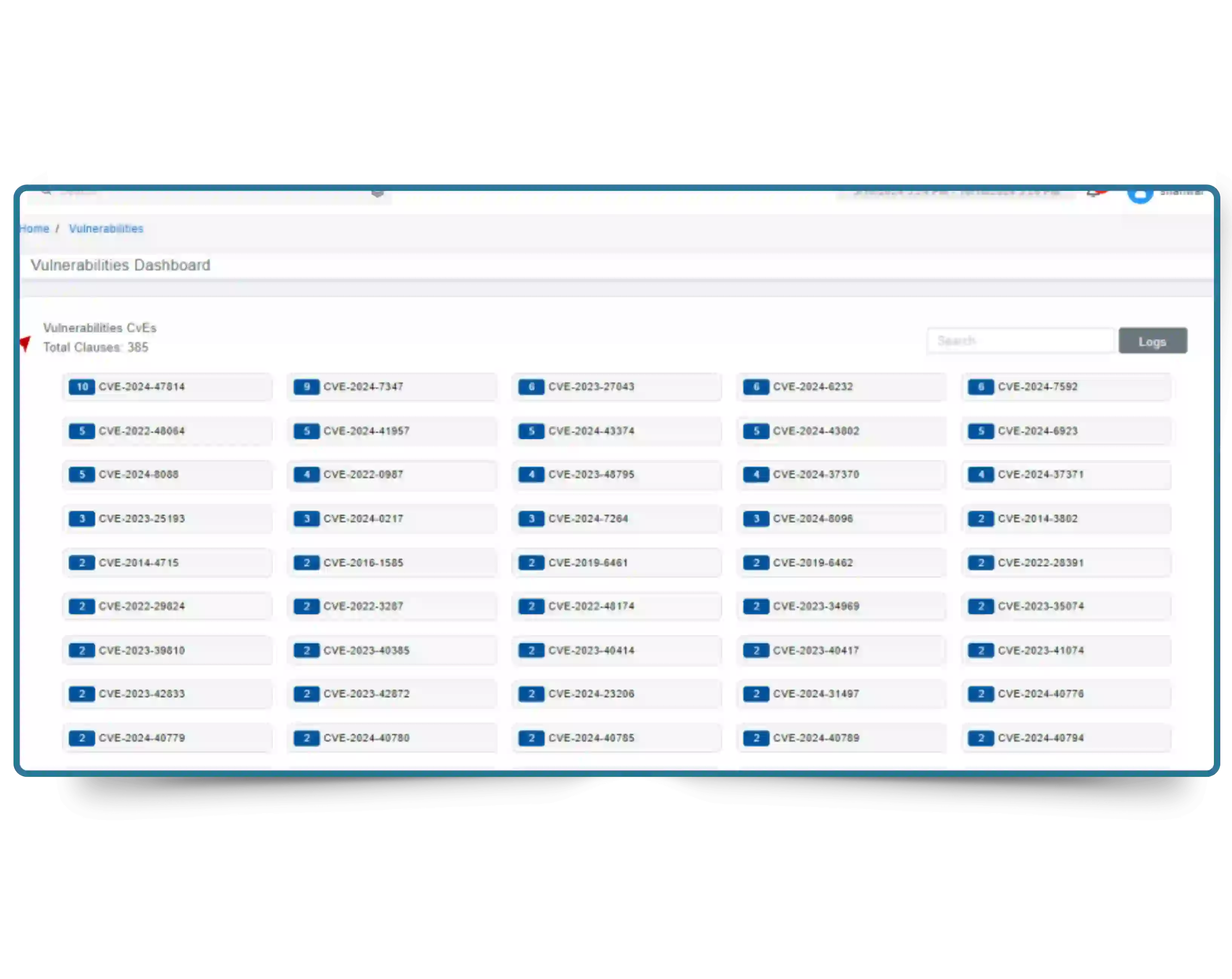
Not every tool fits your network. Let's walk through how this works for your setup,
compliance needs, and current tools before risks grow.
TEM helps you stay ahead of attackers by continuously monitoring your infrastructure, detecting vulnerabilities early, and guiding swift remediation, so your risk exposure never gets a head start.
Before you start, get a detailed
rollout plan based on your assets, tools, and risk levels. No confusion. No surprises.
Assign remediation tasks, task changes, and manage vulnerability resolution from a unified dashboard.
Use playbooks to whitelist trusted software and prevent unauthorized packages enhancing endpoint security.
Export reports in PDF/CSV. Demonstrate regulatory compliance while proving proactive security controls are in place.
The Exploit Prediction Scoring System (EPSS) helps prioritize vulnerabilities most likely to be exploited soon. It complements CVSS by predicting real-world attack probability, boosting your threat detection strategy and reducing wasted effort on low-risk issues.
| Features | Traditional Vendors | Threat Exposure Management (TEM) |
|---|---|---|
| Continuous Scanning | Scheduled scans (daily/weekly); may use agents or agentless methods but lack always‑on coverage and auto‑discovery | Agent‑based & agentless, 24/7 real‑time discovery and scanning across on‑prem, cloud & hybrid assets |
| CVSS v3/v4 Scoring | Typically limited to CVSS v3; few vendors support the newer v4 metrics | Full support for CVSS v3 and v4, automatically calculating standardized severity metrics for all detected CVEs |
| EPSS Exploit Prediction | No native exploit‑prediction; prioritization relies on static CVSS scores and external intelligence | Built‑in EPSS engine forecasts real‑world exploit likelihood, optimizing vulnerability prioritization |
| Dashboards & Analytics | Fixed dashboard layouts with pre‑built compliance reports and trend charts; limited customization and drill‑down capabilities | Interactive, customizable dashboards, Top 5 High‑Risk CVEs, Impacted Software, Open vs Resolved Issues, attack‑surface heatmaps, compliance status |
| Remediation Guidance | No embedded guidance; remediation instructions must be sourced separately or via external documentation | Contextual, asset‑specific remediation steps (patch links, configuration changes, mitigation playbooks) provided directly in the UI |
| Automated Remediation Workflows | Manual ticket hand‑off to ITSM tools (e.g., ServiceNow, JIRA); no integrated playbook execution | End‑to‑end playbooks for task assignment, SLA tracking, software whitelisting, and automated patch orchestration |
| Real‑time Exposure Alerts | Alerts tied to scan schedules; delayed notifications, higher false‑positive rates, and minimal filtering options | Instant, context‑aware notifications (email, Slack, Teams, PagerDuty) for new or escalating vulnerabilities, with noise‑reduction filters |
Flexible Pricing, Built Around Your Attack Surface Cyber Silo's TEM adapts to your infrastructure, asset volume, and cybersecurity goals, so you only pay for the threat coverage you need. Whether you're managing a handful of endpoints or monitoring global hybrid environments, our pricing scales with your evolving exposure and remediation needs.


"We reduced patching delays by 60% using TEM Tool's continuous scanning and vulnerability tracking."

"The CVE dashboards are intuitive, we now prioritize real threats in minutes."

"A complete vulnerability management tool with excellent network device visibility and EPSS scoring."
Threats don't wait and neither should you. Get ahead of the next exploit with full protection across every asset.
©Cybersilo 2025 - All Rights Reserved